Security News

US and Dutch law enforcement, with the help of Lumen researchers, have disrupted 5socks and Anyproxy, two proxy-for-rent services that were used by criminals for ad fraud and DDoS and brute-force...

The FBI also issued a list of end-of-life routers you need to replace Earlier this week, the FBI urged folks to bin aging routers vulnerable to hijacking, citing ongoing attacks linked to TheMoon...

A joint law enforcement operation undertaken by Dutch and U.S. authorities has dismantled a criminal proxy network that's powered by thousands of infected Internet of Things (IoT) and end-of-life...

The FBI warns that threat actors are deploying malware on end-of-life (EoL) routers to convert them into proxies sold on the 5Socks and Anyproxy networks. [...]
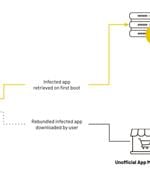
At least four different threat actors have been identified as involved in an updated version of a massive ad fraud and residential proxy scheme called BADBOX, painting a picture of an...

A malicious botnet called Socks5Systemz is powering a proxy service called PROXY.AM, according to new findings from Bitsight. "Proxy malware and services enable other types of criminal activity...

The malware known as Ngioweb has been used to fuel a notorious residential proxy service called NSOCKS, as well as by other services such as VN5Socks and Shopsocks5, new findings from Lumen...

Security researchers are warning that China-linked state-backed hackers are increasingly relying on a vast proxy server network created from virtual private servers and compromised online devices for cyberespionage operations. Called operational relay box networks, these proxy meshes are administered by independent cybercriminals that provide access to multiple state-sponsored actors.

Identity and access management (IAM) services provider Okta has warned of a spike in the "frequency and scale" of credential stuffing attacks aimed at online services. These unprecedented attacks,...

A botnet previously considered to be rendered inert has been observed enslaving end-of-life (EoL) small home/small office (SOHO) routers and IoT devices to fuel a criminal proxy service called...