Security News

The risk of falling victim to fraud is a constant concern for individuals, businesses, and organizations alike. As technology evolves, so too do the methods employed by fraudsters, making fraud prevention an increasingly critical and complex endeavor.

Nearly 70% of businesses said that fraud losses have increased in recent years and most businesses reported that they plan to increase their fraud management budgets by at least 8% to as much as 19%. Despite their plans to increase their fraud prevention budgets, data shows that businesses may not be completely aligned with consumer expectations. Enable real-time fraud detection: Machine learning can help businesses detect and prevent fraud threats in real time, helping to identify both known and unknown threats to stay ahead of fraudsters.

Ecommerce platforms are incorporating sophisticated fraud detection measures, but fraudsters, too, are refining their strategies. In this Help Net Security interview, Eduardo Mônaco, CEO at ClearSale, explains the complexities of ecommerce fraud, discussing the evolution of fraudster tactics, the effectiveness of social footprint analysis in confirming identity, the balance between fraud prevention and customer experience, and techniques to address more advanced fraud types.

Learn actionable tactics for IT departments on how to manage backups and enable staff so that ransomware is no longer a mythical threat, but a controlled risk. Secure Backup is your best line of...
Spear Phishing with Social Engineering: AI can analyze vast amounts of publicly available data from social media, professional networks, or other sources to gather information about potential targets. Regulation and legal risks associated with AI refer to the potential liabilities and legal consequences that businesses may face when implementing AI technology.

Data loss prevention enables organizations to protect their sensitive data. Data loss prevention is a set of software tools, processes and data security practices that help prevent unauthorized access, misuse or loss of sensitive or critical data.

Although CISA doesn't provide specific password recommendations in the ransomware guidance, it recommends following the NIST password security guidelines. In one analysis it was discovered 83% of compromised passwords satisfy the password length and complexity requirements of regulatory password standards.

Every year hundreds of millions of malware attacks occur worldwide, and every year businesses deal with the impact of viruses, worms, keyloggers, and ransomware. Businesses need to defend against malware entering the network, and then on top of that have systems and processes in place to restrict the damage that malware can do if it infects a user device.

ESET researchers have uncovered a compromise of an East Asian data loss prevention company. The attackers utilized at least three malware families during the intrusion, compromising both the internal update servers and third-party tools utilized by the company.
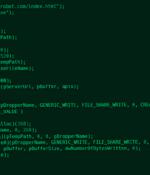
A cyberespionage actor known as Tick has been attributed with high confidence to a compromise of an East Asian data-loss prevention company that caters to government and military entities. "The attackers compromised the DLP company's internal update servers to deliver malware inside the software developer's network, and trojanized installers of legitimate tools used by the company, which eventually resulted in the execution of malware on the computers of the company's customers," ESET researcher Facundo Muñoz said.