Security News

A new multi-stage attack has been observed delivering malware families like Agent Tesla variants, Remcos RAT, and XLoader. "Attackers increasingly rely on such complex delivery mechanisms to evade...
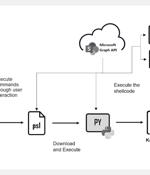
Cybersecurity researchers are calling attention to a new phishing campaign that employs the ClickFix technique to deliver an open-source command-and-control (C2) framework called Havoc. "The...
A nation-state threat actor with ties to North Korea has been linked to an ongoing campaign targeting South Korean business, government, and cryptocurrency sectors. The attack campaign, dubbed...

North Korean state actor 'Kimsuky' (aka 'Emerald Sleet' or 'Velvet Chollima') has been observed using a new tactic inspired from the now widespread ClickFix campaigns. [...]

The North Korea-linked threat actor known as Kimsuky has been observed using a new tactic that involves deceiving targets into running PowerShell as an administrator and then instructing them to...

A previously undocumented threat actor known as Silent Lynx has been linked to cyber attacks targeting various entities in Kyrgyzstan and Turkmenistan. "This threat group has previously targeted...

Threat actors on X are exploiting the news around Ross Ulbricht to direct unsuspecting users to a Telegram channel that tricks them into executing PowerShell code that infects them with malware. [...]
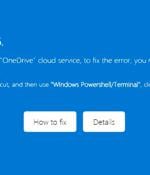
Cybersecurity researchers are warning about a new phishing campaign that targets Microsoft OneDrive users with the aim of executing a malicious PowerShell script. The cybersecurity company is tracking the "Crafty" phishing and downloader campaign under the name OneDrive Pastejacking.

The latest variants of the ViperSoftX info-stealing malware use the common language runtime (CLR) to load and execute PowerShell commands within AutoIt scripts to evade detection. [...]

Fake IT support sites promote malicious PowerShell "Fixes" for common Windows errors, like the 0x80070643 error, to infect devices with information-stealing malware. According to eSentire, threat actors are creating numerous fake IT support sites that are specifically designed to help users with common Windows errors, heavily focusing on the 0x80070643 error.