Security News

Security researchers have shared technical details for exploiting a critical Microsoft Outlook vulnerability for Windows that allows hackers to remotely steal hashed passwords by simply receiving an email. The issue is a privilege escalation vulnerability with a 9.8 severity rating that affects all versions of Microsoft Outlook on Windows.

Veeam Backup & Replication admins, get patching!Veeam Software has patched CVE-2023-27532, a high-severity security hole in its widely-used Veeam Backup & Replication solution, and is urging customer to implement the fix as soon as possible. Fortinet plugs critical RCE hole in FortiOS, FortiProxyFortinet has patched 15 vulnerabilities in a variety of its products, including CVE-2023-25610, a critical flaw affecting devices running FortiOS and FortiProxy.

A PoC exploit for CVE-2023-21716, a critical RCE vulnerability in Microsoft Word that can be exploited when the user previews a specially crafted RTF document, is now publicly available.Patches for the flaw - which affects a wide variety of MS Office and SharePoint versions, Microsoft 365 Apps for Enterprise and other products - have been released by Microsoft last month.

Horizon3's Attack Team has released a PoC exploit for CVE-2022-39952, a critical vulnerability affecting FortiNAC, Fortinet's network access control solution. "Similar to the weaponization of previous archive vulnerability issues that allow arbitrary file write, we use this vulnerability to write a cron job to /etc/cron.d/payload. This cron job gets triggered every minute and initiates a reverse shell to the attacker," shared Zach Hanley, Chief Attack Engineer at Horizon3.

Fortinet has dropped fixes for 40 vulnerabilities in a variety of its products, including two critical vulnerabilities affecting its FortiNAC and FortiWeb solutions.Since cyberattackers love to exploit vulnerabilities in Fortinet enterprise solutions and a PoC exploit for CVE-2022-39952 is expected to be released soon, admins are advised to get a move on patching.

Lexmark has released a security firmware update to fix a severe vulnerability that could enable remote code execution on more than 100 printer models. "Lexmark is not aware of any malicious use against Lexmark products of the vulnerability described in this advisory, but proof of concept code has been publicly published" - Lexmark.
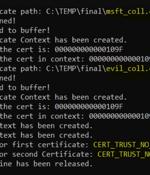
Proof-of-concept (Poc) code has been released for a now-patched high-severity security flaw in the Windows CryptoAPI that the U.S. National Security Agency (NSA) and the U.K. National Cyber...

Akamai researchers have published a PoC exploit for a critical vulnerability in Windows CryptoAPI, which validates public key certificates. "An attacker could manipulate an existing public x.509 certificate to spoof their identity and perform actions such as authentication or code signing as the targeted certificate," Microsoft said in October 2022, when they announced fixes for vulnerable Windows and Windows Server versions.

Two vulnerabilities found in three NetComm router models could be exploited to achieve remote code execution on vulnerable devices, and there's a public PoC chaining them, CERT/CC has warned. CVE-2022-4874 is an authentication bypass flaw and CVE-2022-4873 is a stack based buffer overflow vulnerability that allows attackers to crash the application at a known location and exploit that to execute code on a vulnerable device.

If your enterprise is running ManageEngine products that were affected by CVE-2022-47966, check now whether they've been updated to a non-vulnerable version because Horizon3's will be releasing technical details and a PoC exploit this week. CVE-2022-47966 is an unauthenticated remote code execution vulnerability that has been found by a researcher with Viettel Cyber Security in two dozen ManageEngine products, including Access Manager Plus, ADSelfService Plus, Endpoint DLP, Password Manager Pro, PAM360, ServiceDesk Plus, and others.