Security News

Microsoft is top of the heap when it comes to hacker impersonations - with Microsoft products and services featuring in nearly a fifth of all global brand phishing attacks in the third quarter of this year. The top three phishing brands exploited by email phishing attacks were Microsoft, DHL and Apple; on the web, it was Microsoft, Google and PayPal; and for mobile, WhatsApp, PayPal and Facebook took the top spots.

Cybercriminals cashed in on the surge of COVID-19 earlier this year, with email lures purporting to be from healthcare professionals offering more information about the pandemic. As the year moves forward, bad actors are continuing to swap up their attacks with savvy lures that match top-of-mind current events, said Derek Manky, Chief of Security Insights & Global Threat Alliances at Fortinet's FortiGuard Labs.

Hackers needed roughly 24 hours to take over high-profile Twitter accounts in the July attack, a report from the New York Department of Financial Services reveals. A couple of weeks after the incident, Twitter revealed that hackers targeted some employees with phone phishing until gaining access to the account support tools they needed.

Iran-linked state-sponsored threat actor 'Silent Librarian' has launched another phishing campaign targeting universities around the world. Silent Librarian, Malwarebytes' security researchers reveal, has sent spear-phishing emails to both staff and students at the targeted universities, and the threat actor was observed setting up new infrastructure to counter efforts to take down its domains.

Free graphics design website Canva is being abused by threat actors to create and host intricate phishing landing pages. Canva is a graphic design platform that lets users create posters, letterheads, holiday cards, and other digital media that can then be downloaded as an image, shared as HTML with clickable links, or printed.

The Qbot botnet uses a new template for the distribution of their malware that uses a fake Windows Defender Antivirus theme to trick you into enabling Excel macros. Qbot, otherwise known as QakBot or QuakBot, is Windows malware that steals bank credentials, Windows domain credentials, and provides remote access to threat actors who install ransomware.

Analysis of hundreds of millions of web pages found phishing and fraudulent sites using the Amazon brand and logos poised for big Prime Day sales, according to Bolster Research. Analysis of hundreds of millions of web pages led to tracking new phishing and fraudulent websites using the Amazon brand and logos-the fake sites are trying to replicate the actual Amazon site in the hopes of hacking into the unsuspecting "Customer's" personal information.
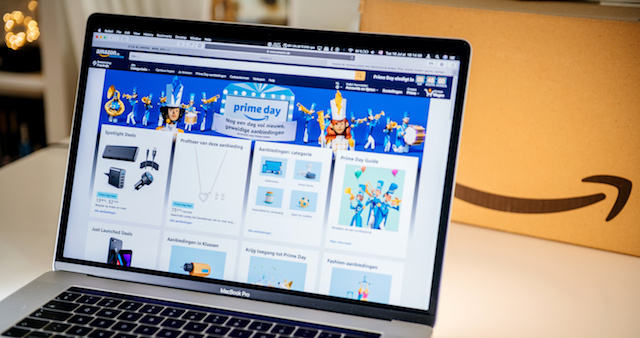
Cybercriminals are tapping into Amazon's annual discount shopping campaign for subscribers, Prime Day, with researchers warning of a recent spike in phishing and malicious websites that are fraudulently using the Amazon brand. There has been a spike in the number of new monthly phishing and fraudulent sites created using the Amazon brand since August, the most significant since the COVID-19 pandemic forced people indoors in March, according to a Thursday report from Bolster Research.

Microsoft announced that consent phishing protections including OAuth app publisher verification and app consent policies are now generally available in Office 365. These protections are designed to defend Office 365 users from an application-based phishing attack variant known as consent phishing.

A phishing campaign pushing a network-compromising backdoor pretends to have the inside scoop on President Trump's health after being infected with COVID-19. To capitalize on this, the threat actors behind the BazarLoader trojan have started a new phishing campaign that pretends to have insider information on Trump's condition.