Security News

The Federal Bureau of Investigation warned today of recently detected spear-phishing email campaigns targeting customers of "Brand-name companies" in attacks known as brand phishing.In addition to these ongoing phishing attacks, threat actors are also likely developing tools to bait potential targets into revealing info for bypassing account protections two-factor authentication by intercepting emails and compromising accounts.

Secure email gateway protections aren't necessarily enough to stop phishing emails from delivering ransomware to employees, especially if the cybercrooks are using legitimate cloud services to host malicious pages. Researchers are raising the alarm over a phishing email kicking off a Halloween-themed MICROP ransomware offensive, which they observed making its way to a target's inbox despite its being secured by an SEG. Infection Routine.

Phishing emails are now skating past traditional defenses. Even with the most sophisticated email scanning and phishing detection system available, phishing emails are still a very common intrusion vector for cybercriminals to use to introduce malware, including ransomware, to a business' network.

Phishing actors are now actively abusing the Glitch platform to host short-lived credential-stealing URLs for free while evading detection and takedowns. Glitch is a cloud hosting service that allows people to deploy apps and websites using Node.js, React, and other development platforms.

A long-term spear-phishing campaign is targeting employees of major corporations with emails containing PDFs that link to short-lived Glitch apps hosting credential-harvesting SharePoint phishing pages, researchers have found. Instead, the malicious activity propagated by the PDFs is a link to Glitch apps hosting phishing pages that included obfuscated JavaScript for stealing credentials, he wrote.
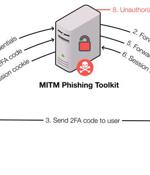
The findings come from a new study undertaken by a group of researchers from Stony Brook University and Palo Alto Networks, who have demonstrated a new fingerprinting technique that makes it possible to identify MitM phishing kits in the wild by leveraging their intrinsic network-level properties, effectively automating the discovery and analysis of phishing websites. Dubbed "PHOCA" - named after the Latin word for "Seals" - the tool not only facilitates the discovery of previously unseen MitM phishing toolkits, but also be used to detect and isolate malicious requests coming from such servers.

Researchers have observed a new phishing campaign primarily targeting high-profile TikTok accounts belonging to influencers, brand consultants, production studios, and influencers' managers. In some cases seen by Abnormal Security, the actors impersonate TikTok employees, threatening the recipient with imminent account deletion due to an alleged violation of the platform's terms.

A recently discovered phishing scam tried to takeover more than 125 high-profile user accounts on TikTok. Researchers at cloud email security provider Abnormal Security detected the scams that attempted to take over people's accounts by sending emails impersonating TikTok and asking users to verify their log-in information.
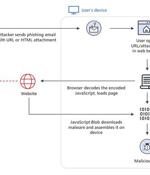
Threat actors are increasingly banking on the technique of HTML smuggling in phishing campaigns as a means to gain initial access and deploy an array of threats, including banking malware, remote administration trojans, and ransomware payloads. HTML smuggling is an approach that allows an attacker to "Smuggle" first-stage droppers, often encoded malicious scripts embedded within specially-crafted HTML attachment or web pages, on a victim machine by taking advantage of basic features in HTML5 and JavaScript rather than exploiting a vulnerability or a design flaw in modern web browsers.

Learn how to detect phishing on LinkedIn and protect yourself from it. Abusing LinkedIn is one of those techniques that is very effective because a lot of professionals use and depend on LinkedIn for their activities or work relationships.