Security News

These attacks can lead to the bypassing of phishing detection and email security solutions, and at the same time, gives phishing URLs a false snse of legitimacy to victims. "The attacks use dozens of distinct Microsoft 365 third-party applications with malicious redirect URLs defined for them," explains Proofpoint's report.

A new phishing campaign analyzed by email security provider Avanan exploits a key feature in Microsoft Outlook. To use Outlook against its users, hackers simply start by devising a phishing email that appears to be sent from an actual person.

US universities are being targeted in multiple phishing attacks designed to impersonate college login portals to steal valuable Office 365 credentials. These campaigns are believed to be conducted by multiple threat actors starting in October 2021, with Proofpoint sharing details on the tactics, techniques, and procedures used in the phishing attacks.

A persuasive and ongoing series of phishing attacks are using fake Office 365 notifications asking the recipients to review blocked spam messages, with the end goal of stealing their Microsoft credentials. Instead of reaching the Office 365 portal when clicking the 'Review' button, they are sent to a phishing landing page that will ask them to enter their Microsoft credentials to access the quarantined spam messages.

A new phishing campaign has been targeting verified Twitter accounts, as seen by BleepingComputer. Verified accounts on Twitter refer to those possessing a blue badge with a checkmark.

A new phishing campaign has been targeting verified Twitter accounts, as seen by BleepingComputer. The phishing campaign follows Twitter's recent removal of the checkmarks from a number of verified accounts, citing that these were ineligible for the legendary status, and were verified in error.

The global pandemic has provided cover for all sorts of phishing scams over the past couple of years, and the rise in alarm over the spread of the latest COVID-19 variant, Omicron, is no exception. U.K. consumer watchdog "Which?" has raised the alarm that a new phishing scam, doctored up to look like official communications from the National Health Service, is targeting people with fraud offers for free PCR tests for the COVID-19 Omicron variant.

Research conducted by Egress and Orpheus Cyber has revealed a surge in phishing kits imitating major brands in the lead up to Black Friday, as security experts warn that cybercriminals are stepping up their phishing attacks over the holiday shopping season. Amazon was a popular choice for cybercriminals, with a 334.1% increase in phishing kits impersonating the brand ahead of its anticipated Black Friday promotions.

Phishing actors have quickly started to exploit the emergence of the Omicron COVID-19 variant and now use it as a lure in their malicious email campaigns. Threat actors are quick to adjust to the latest trends and hot topics, and increasing people's fears is an excellent way to cause people to rush to open an email without first thinking it through.
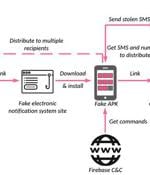
Socially engineered SMS messages are being used to install malware on Android devices as part of a widespread phishing campaign that impersonates the Iranian government and social security services to make away with credit card details and steal funds from victims' bank accounts. "The malicious application not only collects the victim's credit card numbers, but also gains access to their 2FA authentication SMS, and turn[s] the victim's device into a bot capable of spreading similar phishing SMS to other potential victims," Check Point researcher Shmuel Cohen said in a new report published Wednesday.