Security News

A phishing campaign was observed predominantly targeting a notable energy company in the US, employing QR codes to slip malicious emails into inboxes and bypass security. According to Cofense, who spotted this campaign, this is the first time that QR codes have been used at this scale, indicating that more phishing actors may be testing their effectiveness as an attack vector.

Threat actors' use of Cloudflare R2 to host phishing pages has witnessed a 61-fold increase over the past six months. "The majority of the phishing campaigns target Microsoft login credentials, although there are some pages targeting Adobe, Dropbox, and other cloud apps," Netskope security researcher Jan Michael said.

Is your organization constantly under threat from credential phishing? Even with comprehensive security awareness training, many employees still fall victim to credential phishing scams. What if you could outsmart these criminals and protect your organization?

New research from Proofpoint exposes a new massive credential phishing attack campaign aimed at top-level executives in more than 100 organizations worldwide. This cybersecurity attack leverages the EvilProxy phishing kit and bypasses two-factor authentication.
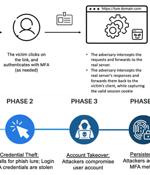
Threat actors are increasingly using a phishing-as-a-service toolkit dubbed EvilProxy to pull off account takeover attacks aimed at high-ranking executives at prominent companies. According to Proofpoint, an ongoing hybrid campaign has leveraged the service to target thousands of Microsoft 365 user accounts, sending approximately 120,000 phishing emails to hundreds of organizations worldwide between March and June 2023.

Interpol has announced the takedown of a phishing-as-a-service platform called 16Shop, in addition to the arrests of three individuals in Indonesia and Japan. 16Shop specialized in the sales of phishing kits that other cybercriminals can purchase to mount phishing attacks on a large scale, ultimately facilitating the theft of credentials and payment details from users of popular services such as Apple, PayPal, American Express, Amazon, and Cash App, among others.

EvilProxy is becoming one of the more popular phishing platforms to target MFA-protected accounts, with researchers seeing 120,000 phishing emails sent to over a hundred organizations to steal Microsoft 365 accounts. A new phishing campaign observed by Proofpoint since March 2023 is using the EvilProxy service to send emails that impersonate popular brands like Adobe, DocuSign, and Concur.

INTERPOL has revealed a successful investigation into a phishing-as-a-service operation named "16shop" with arrests of alleged operators made in Indonesia and Japan and the platform shut down. The operation against 16Shop involved intelligence-sharing between the INTERPOL General Secretariat's cyber crime directorate, plus authorities in Indonesia, Japan and the United States.

A joint operation between Interpol and cybersecurity firms has led to an arrest and shutdown of the notorious 16shop phishing-as-a-service platform. Phishing-as-a-service platforms offer cybercriminals a one-stop-shop to conduct phishing attacks.

Microsoft on Wednesday disclosed that it identified a set of highly targeted social engineering attacks mounted by a Russian nation-state threat actor using credential theft phishing lures sent as Microsoft Teams chats. Microsoft said the campaign, observed since at least late May 2023, affected less than 40 organizations globally spanning government, non-government organizations, IT services, technology, discrete manufacturing, and media sectors.