Security News

A new, lightweight variant of the RomCom backdoor was deployed against participants of the Women Political Leaders Summit in Brussels, a summit focusing on gender equality and women in politics. Designed to imitate the real Women Political Leaders website hosted on wplsummit.org.
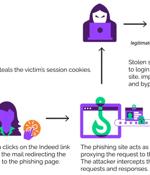
Senior executives working in U.S.-based organizations are being targeted by a new phishing campaign that leverages a popular adversary-in-the-middle (AiTM) phishing toolkit named EvilProxy to...
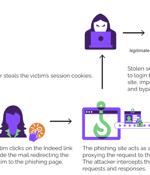
Microsoft, the Dark Web and the name John Malkovich all factor into this EvilProxy phishing attack. A new EvilProxy phishing attack is leveraging an open redirection flaw from the legitimate Indeed.com job search site, according to a report from Menlo Security, a cloud-based security company.

Google will introduce new sender guidelines in February to bolster email security against phishing and malware delivery by mandating bulk senders to authenticate their emails and adhere to stricter spam thresholds. Starting February 1st, 2024, Google will require senders dispatching over 5,000 messages daily to Gmail accounts to set up SPF/DKIM and DMARC email authentication for their domains to strengthen defenses against email spoofing and phishing attempts.

A recently uncovered phishing campaign is targeting Microsoft 365 accounts of key executives in U.S.-based organizations by abusing open redirects from the Indeed employment website for job listings. In August 2023, Proofpoint warned of another EvilProxy campaign, which distributed approximately 120,000 phishing emails to hundreds of organizations, targeting their employees' Microsoft 365 accounts.
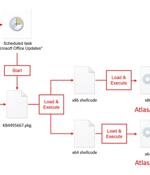
A new threat actor known as AtlasCross has been observed leveraging Red Cross-themed phishing lures to deliver two previously undocumented backdoors named DangerAds and AtlasAgent. NSFOCUS...

Cybercriminals are leveraging the ZeroFont technique to trick users into trusting phishing emails, SANS ISC handler Jan Kopriva has warned. Documented and named by Avanan in 2018, the ZeroFont technique involves using text written in font size "0" throughout the email body.

Hackers are utilizing a new trick of using zero-point fonts in emails to make malicious emails appear as safely scanned by security tools in Microsoft Outlook. The ZeroFont attack method, first documented by Avanan in 2018, is a phishing technique that exploits flaws in how AI and natural language processing systems in email security platforms analyze text.

A new APT hacking group named 'AtlasCross' targets organizations with phishing lures impersonating the American Red Cross to deliver backdoor malware. Cybersecurity firm NSFocus identified two previously undocumented trojans, DangerAds and AtlasAgent, associated with attacks by the new APT group.
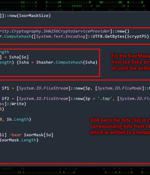
Ukrainian military entities are the target of a phishing campaign that leverages drone manuals as lures to deliver a Go-based open-source post-exploitation toolkit called Merlin. "Since drones or...