Security News

About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I've been writing about security issues on my blog since 2004, and in my monthly newsletter since 1998.
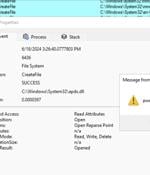
Threat actors are exploiting a novel attack technique in the wild that leverages specially crafted management saved console (MSC) files to gain full code execution using Microsoft Management...

Researchers at Graz University of Technology were able to spy on users' online activities simply by monitoring fluctuations in the speed of their internet connection. This stealthy approach allows the attacker to reconstruct the victim's online activity, posing a threat to their privacy.

P2PInfect, originally a dormant peer-to-peer malware botnet with unclear motives, has finally come alive to deploy a ransomware module and a cryptominer in attacks on Redis servers. P2PInfect was first documented in July 2023 by Unit 42 researchers, targeting Redis servers using known vulnerabilities.

Browser security is becoming increasingly popular, as organizations understand the need to protect at the point of risk - the browser. Network and endpoint solutions are limited in their ability...
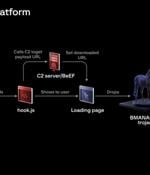
A previously undocumented threat actor dubbed Boolka has been observed compromising websites with malicious scripts to deliver a modular trojan codenamed BMANAGER. "The threat actor behind this...

Some attacks - such as 2021's REvil attack on Kaseya - target backup systems first to ensure that backups will be useless after the malware scrambles production data. According to Veeam's 2023 Ransomware Trends Report, 93 percent of cyber attacks last year targeted backup storage to force ransom payments.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

WikiLeaks founder Julian Assange has been freed in the U.K. and has departed the country after serving more than five years in a maximum security prison at Belmarsh for what was described by the...

Unlike an active security device such as a firewall, Zeek operates on a versatile 'sensor' that can be a hardware, software, virtual, or cloud platform. This flexibility allows Zeek to quietly monitor network traffic, interpret it, and generate transaction logs, file content, and customized output.