Security News

Grabbing Discord authentication tokens and files related to Steam and Telegram authentication-related files. Exploiting CVE-2023-36025 allows attackers to bypass Windows Defender SmartScreen checks and associated prompts, which means that when the victim is tricked into dowloading and opening a malicious file, Windows won't warn them against it if the service finds the file suspicious and potentially malicious.

About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I've been writing about security issues on my blog since 2004, and in my monthly newsletter since 1998.

Juniper Networks has fixed a critical pre-authentication remote code execution vulnerability in Junos OS on SRX firewalls and EX switches.CVE-2024-21591 is an out-of-bounds write vulnerability that could allow an unauthenticated, network-based threat actor to carry out a denial-of service attack, an RCE attack, or gain root privileges on exposed devices.

You can choose to see how Rubrik Security Cloud can help your organization reduce complexity, break down silos and deliver consistent data protection across your entire infrastructure for example. Other demos provide a friendly introduction to the company's Ransomware Response Team and show you how Rubrik helps to foil the dastardly cyber criminals which have make the data gold mine that is Microsoft 365 their number one target for ransomware attacks.

Multiple security vulnerabilities have been disclosed in Bosch BCC100 thermostats and Rexroth NXA015S-36V-B smart nutrunners that, if successfully exploited, could allow attackers to execute...

Thousands of WordPress sites using a vulnerable version of the Popup Builder plugin have been compromised with a malware called Balada Injector. First documented by Doctor Web in January 2023, the...

This shift in phishing philosophies has also led to a precipitous decline in the use of malicious payloads in phishing emails - presumably to avoid detection from the more capable email security solutions of today. It appears this inherent constraint on scale is now a thing of the past, with the emergence of generative AI effectively flipping the funnel on phishing speed and scale.
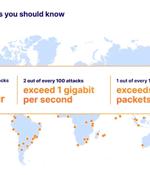
The environmental services industry witnessed an “unprecedented surge” in HTTP-based distributed denial-of-service (DDoS) attacks, accounting for half of all its HTTP traffic. This marks a 61,839%...

In this Help Net Security video, John Morello, CTO of Gutsy, discusses the often-overlooked aspect of cybersecurity - the offboarding process. He outlines the real-world implications and potential impact on an organization's security posture if off-boarding isn't handled thoroughly.

Adalanche provides immediate insights into the permissions of users and groups within an Active Directory. "The visual attack graph representation of your Active Directory pops up in your browser, and you can explore things from there. The more data you add, the more insights you get: if you run the open-source Windows collector, you get local accounts, groups, services, file/registry permissions, etc., from both workstations and servers in the graph."