Security News
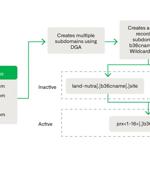
A new DNS threat actor dubbed Savvy Seahorse is leveraging sophisticated techniques to entice targets into fake investment platforms and steal funds. “Savvy Seahorse is a DNS threat actor who...

More than 225,000 logs containing compromised OpenAI ChatGPT credentials were made available for sale on underground markets between January and October 2023, new findings from Group-IB show....

A threat actor specializing in establishing initial access to target organizations' computer systems and networks is using booby-trapped email attachments to steal employees' NTLM hashes. "User authentication in Windows is used to prove to a remote system that a user is who they say they are. NTLM does this by proving knowledge of a password during a challenge and response exchange without revealing the password to anyone," Microsoft said in a recent post that announced their goal to deprecate NTLM use in favor of Kerberos - a more modern, extensible and secure authentication protocol.
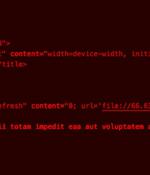
The threat actor known as TA577 has been observed using ZIP archive attachments in phishing emails with an aim to steal NT LAN Manager (NTLM) hashes. The new attack chain “can be used for...

Typically it is energy improvement peddlers or debt help specialists that are disgraced by Britain's data watchdog for spamming unsuspecting households, but the latest entrant in the hall of shame is a charity. The charity was found to have dispatched more than 460,000 unsolicited texts during a ten-day period to 52,000 people that had not consented to receive the messages or had "Clearly opted out," the ICO said.

Understanding risk is one thing, but how do you know if your organization has what it takes to withstand those risks being realized? Establishing cyber maturity can help determine resilience, where the strengths and weaknesses lie, and what needs to happen to improve those security processes. In the face of escalating risks leading to more claims, cyber insurance providers are now pushing for cyber maturity assessments to determine their risk exposure when quoting for policies, for example.

Data protection is relevant to everyone, whether you are handling personal data or your data being processed. It delves into the main data protection applications and explores the rights afforded under these regulations.

In this Help Net Security video, Ryan Amparo, Field Application Engineer at Kingston Technology, discusses the benefits of encrypted external SSDs and USBs for hybrid workforces. He talks about the differences between software and hardware encryption, why it's important, and why usage and cost matter.

Lovejoy discusses the alignment between DORA and NIS2 directives, the timeline for DORA's implementation, and the imperative steps organizations must take to ensure compliance by the 2025 deadline. How will DORA impact organizations across the EU, particularly regarding ICT risk management and cybersecurity?

92% of companies had experienced a breach in the prior year due to vulnerabilities of applications developed in-house, according to Checkmarx. In recent years the responsibility for application security has shifted away from dedicated security teams and is now shared between AppSec managers and developers.