Security News

A newly numbered Windows zero-day vulnerability is being exploited in the wild via specially crafted Office documents, security researchers are warning. Boobytrapped office files delivered via email are one of the most common tactics attackers use to compromise endpoints, and they are constantly finding new ways to hide the documents' malicious nature from existing security defenses, solutions, as well as users/targets.

Infosec researchers have idenitied a zero-day code execution vulnerability in Microsoft's ubiquitous Office software. Dubbed "Follina", the vulnerability has been floating around for a while and uses Office functionality to retrieve a HTML file which in turn makes use of the Microsoft Support Diagnostic Tool to run some code.

A zero-day vulnerability in Microsoft Office allows adversaries to run malicious code on targeted systems via a flaw a remote Word template feature. Noted security researcher Kevin Beaumont dubbed the vulnerability "Follina", explaining the zero day code references the Italy-based area code of Follina - 0438.Beaumont said the flaw is abusing the remote template feature in Microsoft Word and is not dependent on a typical macro-based exploit path, common within Office-based attacks.

Security researchers have discovered a new Microsoft Office zero-day vulnerability that is being used in attacks to execute malicious PowerShell commands via Microsoft Diagnostic Tool simply by opening a Word document.The vulnerability, which has yet to receive a tracking number and is referred to by the infosec community as 'Follina,' is leveraged using malicious Word documents that execute PowerShell commands via the MSDT. This new Follina zero-day opens the door to a new critical attack vector leveraging Microsoft Office programs as it works without elevated privileges, bypasses Windows Defender detection, and does not need macro code to be enabled to execute binaries or scripts.
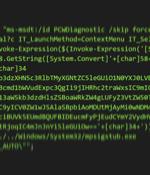
Cybersecurity researchers are calling attention to a zero-day flaw in Microsoft Office that could be abused to achieve arbitrary code execution on affected Windows systems. According to security researcher Kevin Beaumont, who dubbed the flaw "Follina," the maldoc leverages Word's remote template feature to fetch an HTML file from a server, which then makes use of the "Ms-msdt://" URI scheme to run the malicious payload. MSDT is short for Microsoft Support Diagnostics Tool, a utility that's used to troubleshoot and collect diagnostic data for analysis by support professionals to resolve a problem.

Microsoft has improved the account settings in the latest Windows 11 preview build, a settings page that now lists Office subscriptions linked to the user's Microsoft 365 account. The Windows Insider team started rolling out a new 'Your Microsoft account' settings page within Windows 11's Settings in October 2021.

Microsoft has reminded customers earlier this week that Microsoft Office 2013 is approaching its end of support next year, advising them to switch to a newer version to reduce their exposure to security risks. "After five years of Mainstream Support, and five years of Extended Support, Office 2013 will reach the End of Extended Support on April 11, 2023. Per the Fixed Lifecycle Policy, after this date security updates for Office 2013 will no longer be available," Microsoft told customers.

Windows Autopatch is an automated, managed service by Microsoft to keep Windows and Office always up-to-date. "Windows Autopatch manages all aspects of deployment groups for Windows 10 and Windows 11 quality and feature updates, drivers, firmware, and Microsoft 365 Apps for enterprise updates. Drivers and firmware that are published to Windows Update as Automatic will be delivered as part of Windows Autopatch," Lior Bela, a Senior Product Marketing Manager on the Microsoft 365 team, explained.

An unknown Chinese-speaking threat actor has been targeting betting companies in Taiwan, Hong Kong, and the Philippines, leveraging a vulnerability in WPS Office to plant a backdoor on the targeted systems. The first infection vector used in this campaign is an email with a laced installer that pretends to be a critical WPS Office update, but in most attacks, the threat actors use a different method.

Windows admins were hit today by a wave of Microsoft Defender for Endpoint false positives where Office updates were tagged as malicious in alerts pointing to ransomware behavior detected on their systems. Following the surge of reports, Microsoft confirmed the Office updates were mistakenly marked as ransomware activity due to false positives.