Security News

The NSA and FBI warned that the APT43 North Korea-linked hacking group exploits weak email Domain-based Message Authentication Reporting and Conformance policies to mask spearphishing attacks. Together with the U.S. State Department, the two agencies cautioned that the attackers abuse misconfigured DMARC policies to send spoofed emails which appear to come from credible sources such as journalists, academics, and other experts in East Asian affairs.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Microsoft has revealed that North Korea-linked state-sponsored cyber actors has begun to use artificial intelligence (AI) to make its operations more effective and efficient. "They are learning to...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Japan's Computer Security Incident Response Team is warning that the notorious North Korean hacking group Lazarus has uploaded four malicious PyPI packages to infect developers with malware. PyPI is a repository of open-source software packages that software developers can utilize in their Python projects to add additional functionality to their programs with minimal effort.

A set of fake npm packages discovered on the Node.js repository has been found to share ties with North Korean state-sponsored actors, new findings from Phylum show. The packages are named...
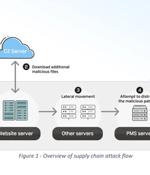
The North Korean state-sponsored threat actors have been attributed to a cyber espionage campaign targeting the defense sector across the world. In a joint advisory published by Germany's Federal...

In an advisory today Germany's federal intelligence agency and South Korea's National Intelligence Service warn of an ongoing cyber-espionage operation targeting the global defense sector on behalf of the North Korean government. Today's joint cybersecurity advisory highlights two cases attributed to North Korean actors, one of them the Lazarus group, to provide the tactics, techniques, and procedures used by the attackers.

The North Korean hacker collective Lazarus, infamous for having carried out numerous large-scale cryptocurrency heists over the years, has switched to using YoMix bitcoin mixer to launder stolen proceeds. Some of the largest cryptocurrency theft operations Lazarus conducted in recent years include the March 2022 Ronin Network hack that yielded $625 million, the Harmony Horizon hack in June 2022 that resulted in losses of $100 million, and the July 2023 Alphapo heist from where the hackers pocketed $60 million worth of crypto.

Media organizations and high-profile experts in North Korean affairs have been at the receiving end of a new campaign orchestrated by a threat actor known as ScarCruft in December 2023. "ScarCruft...