Security News

Zyxel is warning its NAS devices users to update their firmware to fix a critical severity command injection vulnerability. Zyxel has provided no workarounds or mitigations for CVE-2023-27992 in its latest advisory, so users of the impacted NAS devices are recommended to apply the available security updates as soon as possible.

Zyxel has rolled out security updates to address a critical security flaw in its network-attached storage devices that could result in the execution of arbitrary commands on affected systems. Tracked as CVE-2023-27992, the issue has been described as a pre-authentication command injection vulnerability.

Zyxel has released firmware patches for a critical vulnerability in some of its consumer network attached storage devices. CVE-2023-27992 is an OS command injection flaw that could be triggered remotely by an unauthenticated attacker, via a specially crafted HTTP request.

Western Digital is warning owners of My Cloud series devices that can no longer connect to cloud services starting on June 15, 2023, if the devices are not upgraded to the latest firmware, version 5.26.202. "Devices on firmware below 5.26.202 will not be able to connect to Western Digital cloud services starting June 15, 2023, and users will not be able to access data on their device through mycloud.com and the My Cloud OS 5 mobile app until they update the device to the latest firmware," explains a Western Digital support bulletin.

Zyxel has patched a high-severity authenticated command injection vulnerability in some of its network attached storage devices aimed at home users. The vulnerability was discovered in the devices' web management interface.
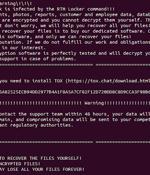
The threat actors behind RTM Locker have developed a ransomware strain that's capable of targeting Linux machines, marking the group's first foray into the open source operating system. "Its locker ransomware infects Linux, NAS, and ESXi hosts and appears to be inspired by Babuk ransomware's leaked source code," Uptycs said in a new report published Wednesday.

Taiwanese hardware vendor QNAP warns customers to secure their Linux-powered network-attached storage devices against a high-severity Sudo privilege escalation vulnerability. The vulnerability also affects the QTS, QuTS hero, QuTScloud, and QVP NAS operating systems, as QNAP revealed in a security advisory published on Wednesday.

The U.S. Cybersecurity and Infrastructure Security Agency on Friday added three flaws to its Known Exploited Vulnerabilities catalog, citing evidence of active abuse in the wild. Details about the flaw were disclosed by Ethiopian cyber security research firm Octagon Networks in March 2022.

QNAP Systems has fixed a critical vulnerability affecting QNAP network-attached storage devices, which could be exploited by remote attackers to inject malicious code into a vulnerable system.Luckily for QNAP NAS owners, there's no mention of it being exploited by attackers or an exploit being publicly available.

Taiwanese company QNAP has released updates to remediate a critical security flaw affecting its network-attached storage devices that could lead to arbitrary code injection. Tracked as CVE-2022-27596, the vulnerability is rated 9.8 out of a maximum of 10 on the CVSS scoring scale.