Security News

MuddyWater, an Iranian government-backed cyber espionage crew, has upgraded its malware with a custom backdoor, which it's used to target Israeli organizations. It's since moved on to phishing campaigns that deploy a new backdoor - dubbed BugSleep - according to Check Point Research.

The Iranian-backed MuddyWatter hacking group has partially switched to using a new custom-tailored malware implant to steal files and run commands on compromised systems. "We discovered several versions of the malware being distributed, with differences between each version showing improvements and bug fixes," Check Point said.

The Iranian threat actor known as MuddyWater has been attributed to a new command-and-control (C2) infrastructure called DarkBeatC2, becoming the latest such tool in its arsenal...

The Iran-affiliated threat actor tracked as MuddyWater (aka Mango Sandstorm or TA450) has been linked to a new phishing campaign in March 2024 that aims to deliver a legitimate Remote Monitoring...
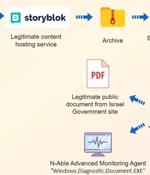
The Iranian nation-state actor known as MuddyWater has been linked to a new spear-phishing campaign targeting two Israeli entities to ultimately deploy a legitimate remote administration tool from...
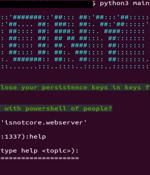
The Iranian state-sponsored group dubbed MuddyWater has been attributed to a previously unseen command-and-control framework called PhonyC2 that's been put to use by the actor since 2021. "MuddyWater is continuously updating the PhonyC2 framework and changing TTPs to avoid detection."
The Iran-linked MuddyWater threat actor has been observed targeting several countries in the Middle East as well as Central and West Asia as part of a new spear-phishing activity. "The campaign...

MuddyWater targets Middle Eastern and Asian countries in phishing attacks. Iranian APT Supergroup MuddyWater has been identified as the hackers linked to attempted phishing attacks against Turkey and other Asian countries according to findings published by Cisco Talos.

Cybersecurity agencies from the U.K. and the U.S. have laid bare a new malware used by the Iranian government-sponsored advanced persistent threat group in attacks targeting government and commercial networks worldwide. "MuddyWater actors are positioned both to provide stolen data and accesses to the Iranian government and to share these with other malicious cyber actors," the agencies said.

US and UK cybersecurity and law enforcement agencies today shared information on new malware deployed by the Iranian-backed MuddyWatter hacking group in attacks targeting critical infrastructure worldwide. MuddyWater is "Targeting a range of government and private-sector organizations across sectors-including telecommunications, defense, local government, and oil and natural gas-in Asia, Africa, Europe, and North America," the two governments said.