Security News

Myanmar's military junta has floated a cyber security law that would ban the use of virtual private networks, under penalty of imprisonment and/or fines, leaving digital rights organisations concerned about the effects of further closing the country off digitally to the outside world. As the country faced a military coup in February 2021, the newly installed Tatmadaw banned Facebook, Instagram, and Twitter, prompting users in the country to rely on VPNs to retain access to their preferred online communication services.
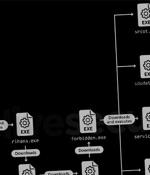
A threat actor with potential links to an Indian cybersecurity company has been nothing if remarkably persistent in its attacks against military organizations based in South Asia, including Bangladesh, Nepal, and Sri Lanka, since at least September 2020 by deploying different variants of its bespoke malware framework. Slovak cybersecurity firm ESET attributed the highly targeted attack to a hacking group known as Donot Team.

U.S. Cyber Command has confirmed that MuddyWater - an advanced persistent threat cyberespionage actor aka Mercury, Static Kitten, TEMP.Zagros or Seedworm that's historically targeted government victims in the Middle East - is an Iranian intelligence outfit. On Wednesday, USCYBERCOM not only confirmed the tie; it also disclosed the plethora of open-source tools and strategies MuddyWater uses to break into target systems and released malware samples.

The US Dept of Commerce's Bureau of Industry and Security has added 27 companies to its list of entities prohibited from doing business with the USA on grounds they threaten national security - and one of the firms is associated with HPE's Chinese joint venture H3C. A preliminary announcement [PDF] of the bans lists a company named New H3C Semiconductor Technologies Co., Ltd on the grounds of its "Support of the military modernization of the People's Liberation Army.". The addresses given by Uncle Sam for this semiconductor business matches those listed on the website of H3C, the Chinese company formed as a joint venture between HPE and Tsinghua Unigroup to build networking products.

The threat actor's goal is Microsoft Office 365 account takeovers. Microsoft, which began tracking the activity in late July 2021, detailed the attacks in an alert released Monday, adding that the culprits appear to be bent on espionage and have ties to Iran.

More than 3,300 U.S. military service members, military dependents and civilians employed by the Department of Defense were compromised as part of a transnational cybercrime ring created to defraud them out of $1.5 million in military benefits from the DoD and the Department of Veterans Affairs. A former civilian medical records technician and administrator with the U.S. Army was at the center of the scheme, according to court documents filed in the U.S. District Court for the Western District of Texas.
Reports that the military has started outfitting firearms with RFID tags for tracking have raised security alarms. The Department of Defense, the Marines and the Navy have already rejected the RFID tagging tech for that specific reason, according to the AP. However, five Air Force bases are operating at least one RFID armory, along with a Florida-based Green Beret unit that uses RFID in what officials said were a "Few" armories.

Cities, states, federal and military agencies should patch the Laserfiche CMS post-haste, said the security researcher whose jaw dropped at 50 sites hosting porn and Viagra spam. Gov domain hosting the offending files and displaying a specific Laserfiche error message.

Three former US intelligence and military operatives broke America's weapons export and computer security laws by, among other things, helping the United Arab Emirates hijack and siphon data from people's iPhones, it emerged on Tuesday. US citizens Marc Baier, 49, and Ryan Adams, 34, and ex-citizen Daniel Gericke, 40, were charged [PDF] with using "Illicit, fraudulent, and criminal means, including the use of advanced covert hacking systems that utilized computer exploits obtained from the United States and elsewhere, to gain unauthorized access to protected computers in the United States and elsewhere and to illicitly obtain information ... from victims from around the world."

Late last year, the NSA declassified and released a redacted version of Lambros D. Callimahos’s Military Cryptanalytics, Part III. We just got most of the index. It’s hard to believe that there...