Security News
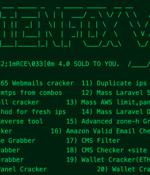
A new "Comprehensive toolset" called AlienFox is being distributed on Telegram as a way for threat actors to harvest credentials from API keys and secrets from popular cloud service providers. "The spread of AlienFox represents an unreported trend towards attacking more minimal cloud services, unsuitable for crypto mining, in order to enable and expand subsequent campaigns," SentinelOne security researcher Alex Delamotte said in a report shared with The Hacker News.

Microsoft's at-times-glitchy Defender service is again causing headaches for IT admins by flagging legitimate URLs as malicious. One Register reader told us: "Our organization has received hundreds of malicious URL alerts from Office 365 for zoom.us links. These false positives take us a long time to investigate. Microsoft finally admitted that this is affecting hundreds of accounts and tenants worldwide."

Microsoft Defender is mistakenly flagging legitimate links as malicious, and some customers have already received dozens of alert emails since the issues began over five hours ago. "We're investigating an issue where legitimate URL links are being incorrectly marked as malicious by the Microsoft Defender service. Additionally, some of the alerts are not showing content as expected," Microsoft said.

Microsoft has unveiled Security Copilot, an AI-powered analysis tool that aims to simplify, augment and accelerate security operations professionals' work. Security Copilot takes the form of a prompt bar through which security operation center analysts ask questions in natural language and receive practical responses.

Microsoft has introduced Microsoft Incident Response Retainer, allowing customers to pre-pay and count on help from Microsoft incident responders before, during and after a cybersecurity crisis.Firms, especially small ones, often don't have dedicated teams that can deal with a cyber incident - they simply don't have the time, resources, or expertise to build an in-house incident response program.
Microsoft on Tuesday unveiled Security Copilot in preview, marking its continued push to embed AI-oriented features in an attempt to offer "End-to-end defense at machine speed and scale."Powered by OpenAI's GPT-4 generative AI and its own security-specific model, it's billed as a security analysis tool that enables cybersecurity analysts to quickly respond to threats, process signals, and assess risk exposure.

Microsoft today announced Security Copilot, a new ChatGPT-like assistant powered by artificial intelligence that takes advantage of Microsoft's threat intelligence footprint to make faster decisions during incident response and to help with threat hunting and security reporting. "Microsoft Security Copilot is an AI-powered security analysis tool that enables analysts to respond to threats quickly, process signals at machine speed, and assess risk exposure in minutes," Redmond says.
New York law firm Heidell, Pittoni, Murphy and Bach has agreed to pay $200,000 to settle a data-breach lawsuit related to the now-notorious Hafnium Microsoft Exchange attacks that siphoned sensitive data from victims around the world. New York Attorney General Letitia James, who brought the lawsuit against the lawyers, blamed HPMB's poor data security practices for the privacy breach.

Traditional, well-behaved image viewers, including the very tool you just used to crop the file, would ignore the extra data, but deliberately-coded data recovery or snooping apps might not. The low-level details of the bug were different, not least because Google's app was coded in Java and used Java libraries, while Microsoft's apps are written in C++ and use Windows libraries, but the leaky side-effects were identical.

Microsoft has unveiled a faster and redesigned version of its Microsoft Teams communication and collaboration software that has begun rolling out to Windows users today as a preview release. The company describes the new Teams client as being twice as faster and consuming 50% less memory and up to 70% less disk space when compared to the current app.