Security News

Google Cloud's recently acquired security outfit Mandiant has named a new nasty from North Korea: a cyber crime gang it calls APT43 and accuses of a five-year rampage. "Mandiant assesses with high confidence that APT43 is a moderately sophisticated cyber operator that supports the interests of the North Korean regime," states a report on the gang released on Wednesday.

Clipboard-injector malware disguised as Tor browser installers has been used to steal about $400,000 in cryptocurrency from nearly 16,000 users worldwide so far in 2023, according to Kaspersky researchers. "The Tor Project called to help keep Russian users connected to Tor to circumvent censorship," Vitaly Kamluk, head of Kaspersky's Global Research and Analysis Team for APAC, wrote in a blog about the clipper malware.

Nexus malware is an Android banking trojan promoted via a malware-as-a-service model. In an underground cybercrime forum ad, the malware project is described as "Very new" and "Under continuous development." More messages from the Nexus author in one forum thread indicate the malware code has been created from scratch.

An unknown Chinese state-sponsored hacking group has been linked to a novel piece of malware aimed at Linux servers. "The rootkit has a limited set of features, mainly installing a hook designed for hiding itself."
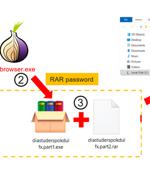
Trojanized installers for the TOR anonymity browser are being used to target users in Russia and Eastern Europe with clipper malware designed to siphon cryptocurrencies since September 2022. "Clipboard injectors can be silent for years, show no network activity or any other signs of presence until the disastrous day when they replace a crypto wallet address," Vitaly Kamluk, director of global research and analysis team for APAC at Kaspersky, said.

A surge of trojanized Tor Browser installers targets Russians and Eastern Europeans with clipboard-hijacking malware that steals infected users' cryptocurrency transactions. While these malicious Tor installers target countries worldwide, Kaspersky says that most are targeting Russia and Eastern Europe.
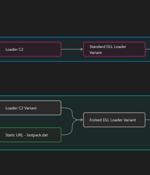
Multiple threat actors have been observed using two new variants of the IcedID malware in the wild with more limited functionality that removes functionality related to online banking fraud. "The well-known IcedID version consists of an initial loader which contacts a Loader server, downloads the standard DLL Loader, which then delivers the standard IcedID Bot," Proofpoint said in a new report published Monday.
A new phishing campaign has set its sights on European entities to distribute Remcos RAT and Formbook via a malware loader dubbed DBatLoader. "The malware payload is distributed through WordPress websites that have authorized SSL certificates, which is a common tactic used by threat actors to evade detection engines," Zscaler researchers Meghraj Nandanwar and Satyam Singh said in a report published Monday.

New IcedID variants have been found without the usual online banking fraud functionality and instead focus on installing further malware on compromised systems. Proofpoint has identified two new variants of the IcedID loader, namely "Lite" and "Forked", both delivering the same IcedID bot with a more narrow-focused feature set.

A new info-stealing malware named MacStealer is targeting Mac users, stealing their credentials stored in the iCloud KeyChain and web browsers, cryptocurrency wallets, and potentially sensitive files. MacStealer is being distributed as a malware-as-a-service, where the developer sells premade builds for $100, allowing purchasers to spread the malware in their campaigns.