Security News
Cybersecurity researchers have detailed the inner workings of a highly evasive loader named "In2al5d p3in4er" that's used to deliver the Aurora information stealer malware. "The in2al5d p3in4er loader is compiled with Embarcadero RAD Studio and targets endpoint workstations using advanced anti-VM technique," cybersecurity firm Morphisec said in a report shared with The Hacker News.

A new Android malware strain named Goldoson has been detected in the official Google Play Store spanning more than 60 legitimate apps that collectively have over 100 million downloads. An additional eight million installations have been tracked through ONE store, a leading third-party app storefront in South Korea.

Ex-Conti ransomware members have teamed up with the FIN7 threat actors to distribute a new malware family named 'Domino' in attacks on corporate networks. Domino is a relatively new malware family consisting of two components, a backdoor named 'Domino Backdoor,' which in turn drops a 'Domino Loader' that injects an info-stealing malware DLL into the memory of another process.
A new QBot malware campaign is leveraging hijacked business correspondence to trick unsuspecting victims into installing the malware, new findings from Kaspersky reveal. QBot is a banking trojan that's known to be active since at least 2007.

Legion targets various services for email exploitation, according to Cado, whose research indicates that Legion is likely linked to the AndroxGh0st malware family first reported in December 2022. The report said Legion appears to be part of an emerging generation of hacking tools that aim to automate the credential harvesting process to compromise SMTP services.
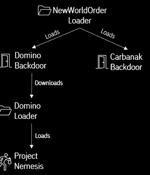
A new strain of malware developed by threat actors likely affiliated with the FIN7 cybercrime group has been put to use by the members of the now-defunct Conti ransomware gang, indicating collaboration between the two crews. The latest intrusion wave, spotted by IBM Security X-Force two months ago, involves the use of Dave Loader, a crypter previously attributed to the Conti group, to deploy the Domino backdoor.

QBot malware is now distributed in phishing campaigns utilizing PDFs and Windows Script Files to infect Windows devices. Qbot is a former banking trojan that evolved into malware that provides initial access to corporate networks for other threat actors.

A new Android trojan called 'Chameleon' has been targeting users in Australia and Poland since the start of the year, mimicking the CoinSpot cryptocurrency exchange, an Australian government agency, and the IKO bank. The mobile malware was discovered by cybersecurity firm Cyble, which reports seeing distribution through compromised websites, Discord attachments, and Bitbucket hosting services.

A new Android malware named 'Goldoson' has infiltrated Google Play through 60 legitimate apps that collectively have 100 million downloads. The malicious malware component is part of a third-party library used by all sixty apps that the developers unknowingly added to their apps.

WhatsApp announced today the introduction of several new security features, one of them dubbed "Device Verification" and designed to provide better protection against account takeover attacks. Device Verification prevents malware from using authentication keys stolen from infected mobile devices or via unofficial clients to impersonate accounts and use them to send scam and phishing messages to people in the targeted users' contact lists.