Security News

The identity of the second threat actor behind the Golden Chickens malware has been uncovered courtesy of a fatal operational security blunder, cybersecurity firm eSentire said. eSentire characterized Jack as the true mastermind behind Golden Chickens.

Two malicious packages discovered in the npm package repository have been found to conceal an open source information stealer malware called TurkoRat. The findings once again underscore the ongoing risk of threat actors orchestrating supply chain attacks via open source packages and baiting developers into downloading potentially untrusted code.
Malicious Google Search ads for generative AI services like OpenAI ChatGPT and Midjourney are being used to direct users to sketchy websites as part of a BATLOADER campaign designed to deliver RedLine Stealer malware. BATLOADER is a loader malware that's propagated via drive-by downloads where users searching for certain keywords on search engines are displayed bogus ads that, when clicked, redirect them to rogue landing pages hosting malware.

Trend Micro has not elaborated on how Lemon Group infects devices with the malicious firmware containing Guerilla but clarified that the devices its analysts examined had been re-flashed with new ROMs. The analysts identified over 50 different ROMs infected with initial malware loaders, targeting various Android device vendors. "The criminal group has infected millions of android devices, mainly mobile phones, but also smart watches, smart TVs and more," reads the description of Trend Micro's Black Hat talk.
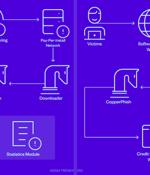
The threat actors behind the CopperStealer malware resurfaced with two new campaigns in March and April 2023 that are designed to deliver two novel payloads dubbed CopperStealth and CopperPhish. Active since at least 2021, Water Orthrus has a track record of leveraging pay-per-install networks to redirect victims landing on cracked software download sites to drop an information stealer codenamed CopperStealer.

The information-stealing malware market is constantly evolving, with multiple malware operations competing for cybercriminal customers by promoting better evasion and increased ability to steal data from victims. Information stealers are specialized malware used to steal account passwords, cookies, credit card details, and crypto wallet data from infected systems, which are then collected into archives called 'logs' and uploaded back to the threat actors.

A new APT hacking group dubbed Lancefly uses a custom 'Merdoor' backdoor malware to target government, aviation, and telecommunication organizations in South and Southeast Asia. The Symantec Threat Labs revealed today that Lancefly has been deploying the stealthy Merdoor backdoor in highly targeted attacks since 2018 to establish persistence, execute commands, and perform keylogging on corporate networks.
Poorly managed Microsoft SQL servers are the target of a new campaign that's designed to propagate a category of malware called CLR SqlShell that ultimately facilitates the deployment of cryptocurrency miners and ransomware. "Similar to web shell, which can be installed on web servers, SqlShell is a malware strain that supports various features after being installed on an MS SQL server, such as executing commands from threat actors and carrying out all sorts of malicious behavior," AhnLab Security Emergency response Center said in a report published last week.
Cybersecurity researchers have discovered an ongoing phishing campaign that makes use of a unique attack chain to deliver the XWorm malware on targeted systems. Securonix, which is tracking the activity cluster under the name MEME#4CHAN, said some of the attacks have primarily targeted manufacturing firms and healthcare clinics located in Germany.
As many as five security flaws have been disclosed in Netgear RAX30 routers that could be chained to bypass authentication and achieve remote code execution. "Successful exploits could allow attackers to monitor users' internet activity, hijack internet connections, and redirect traffic to malicious websites or inject malware into network traffic," Claroty security researcher Uri Katz said in a report.