Security News

A new Mac malware named "Realst" is being used in a massive campaign targeting Apple computers, with some of its latest variants including support for macOS 14 Sonoma, which is still in development. In reality, the game installers infect devices with information-stealing malware, such as RedLine Stealer on Windows and Realst on macOS. This type of malware will steal data from the victim's web browsers and cryptocurrency wallet apps and send them back to the threat actors.

A new Mac malware named "Realst" is being used in a massive campaign targeting Apple computers, with some of its latest variants including support for macOS 14 Sonoma, which is still in development. The malware, first discovered by security researcher iamdeadlyz, is distributed to both Windows and macOS users in the form of fake blockchain games using names such as Brawl Earth, WildWorld, Dawnland, Destruction, Evolion, Pearl, Olymp of Reptiles, and SaintLegend.

Whoever operates the toolkit did not cease activity after Infoblox announced their discovery and published a technical analysis showing that Decoy Dog was heavily based on the Pupy open-source post-exploitation remote access trojan. Some of the changes one Decoy Dog operator made after Infoblox's disclosure was to add a geofencing mechanism that limits responses from controller domains to DNS queries from IP addresses in specific regions.

The analysis of nearly 20 million information-stealing malware logs sold on the dark web and Telegram channels revealed that they had achieved significant infiltration into business environments. The stolen information is packaged into archives called 'logs,' which are then uploaded back to the threat actor for use in attacks or sold on cybercrime marketplaces.
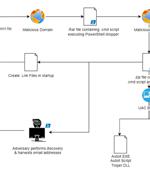
The financially motivated threat actors behind the Casbaneiro banking malware family have been observed making use of a User Account Control bypass technique to gain full administrative privileges on a machine, a sign that the threat actor is evolving their tactics to avoid detection and execute malicious code on compromised assets. Casbaneiro, also known as Metamorfo and Ponteiro, is best known for its banking trojan, which first emerged in mass email spam campaigns targeting the Latin American financial sector in 2018.

The North Korean state-sponsored Lazarus hacking group is breaching Windows Internet Information Service web servers to hijack them for malware distribution. South Korean security analysts at ASEC previously reported that Lazarus was targeting IIS servers for initial access to corporate networks.
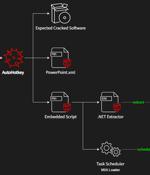
A new variant of AsyncRAT malware dubbed HotRat is being distributed via free, pirated versions of popular software and utilities such as video games, image and sound editing software, and Microsoft Office. "HotRat malware equips attackers with a wide array of capabilities, such as stealing login credentials, cryptocurrency wallets, screen capturing, keylogging, installing more malware, and gaining access to or altering clipboard data," Avast security researcher Martin a Milánek said.

"BundleBot is abusing the dotnet bundle, self-contained format that results in very low or no static detection at all," Check Point said in a report published this week, adding it is "Commonly distributed via Facebook Ads and compromised accounts leading to websites masquerading as regular program utilities, AI tools, and games." NET single-file, self-contained application that, in turn, incorporates a DLL file, whose responsibility is to fetch a password-protected ZIP archive from Google Drive.

Earlier this month, security researchers discovered a new peer-to-peer malware with self-spreading capabilities that targets Redis instances running on Internet-exposed Windows and Linux systems. The Unit 42 researchers who spotted the Rust-based worm on July 11 also found that it hacks into Redis servers that have been left vulnerable to the maximum severity CVE-2022-0543 Lua sandbox escape vulnerability.

Microsoft and the Ukraine CERT warn of new attacks by the Russian state-sponsored Turla hacking group, targeting the defense industry and Microsoft Exchange servers with a new 'DeliveryCheck' malware backdoor. The cyberspies have been associated with a wide array of attacks against Western interests over the years, including the Snake cyber-espionage malware botnet that was recently disrupted in an international law enforcement operation titled Operation MEDUSA. In a coordinated report and Twitter thread published today by CERT-UA and Microsoft, researchers outline a new attack where the Turla threat actors target the defense sector in Ukraine and Eastern Europe.