Security News

Fortinet has issued an alert warning that the Gafgyt botnet malware is actively trying to exploit a vulnerability in the end-of-life Zyxel P660HN-T1A router in thousands of daily attacks. [...]
![New Attack Alert: Freeze[.]rs Injector Weaponized for XWorm Malware Attacks](/static/build/img/news/new-attack-alert-freeze-rs-injector-weaponized-for-xworm-malware-attacks-small.jpg)
Malicious actors are using a legitimate Rust-based injector called Freeze[.]rs to deploy a commodity malware called XWorm in victim environments. The novel attack chain, detected by Fortinet...
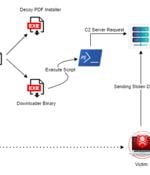
A new information malware strain called Statc Stealer has been found infecting devices running Microsoft Windows to siphon sensitive personal and payment information. "Statc Stealer exhibits a...
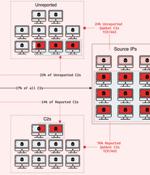
The operators associated with the QakBot malware have set up 15 new command-and-control servers as of late June 2023. The findings are a continuation of the malware's infrastructure analysis from Team Cymru, and arrive a little over two months after Lumen Black Lotus Labs revealed that 25% of its C2 servers are only active for a single day.
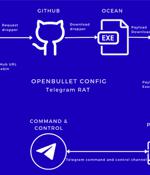
A new malware campaign has been observed making use of malicious OpenBullet configuration files to target inexperienced cyber criminals with the goal of delivering a remote access trojan capable of stealing sensitive information. OpenBullet is a legitimate open-source pen testing tool used for automating credential stuffing attacks.
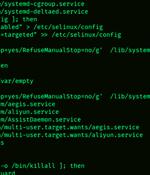
Vulnerable Redis services have been targeted by a "New, improved, dangerous" variant of a malware called SkidMap that's engineered to target a wide range of Linux distributions. "The malicious nature of this malware is to adapt to the system on which it is executed," Trustwave security researcher Radoslaw Zdonczyk said in an analysis published last week.
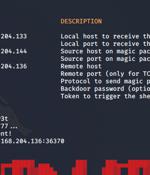
Threat actors are using an open-source rootkit called Reptile to target Linux systems in South Korea. "Unlike other rootkit malware that typically only provide concealment capabilities, Reptile goes a step further by offering a reverse shell, allowing threat actors to easily take control of systems," the AhnLab Security Emergency Response Center said in a report published this week.

The Google Cloud security team acknowledged a common tactic known as versioning used by malicious actors to slip malware on Android devices after evading the Google Play Store's review process and...

The main executable for the Microsoft Publisher application has already been confirmed that it can download payloads from a remote server. According to recent research, even executables that are not signed by Microsoft serve purposes that are useful in attacks, such as reconnaissance.

The malicious Rilide Stealer Chrome browser extension has returned in new campaigns targeting crypto users and enterprise employees to steal credentials and crypto wallets. Rilide is a malicious browser extension for Chromium-based browsers, including Chrome, Edge, Brave, and Opera, that Trustwave SpiderLabs initially discovered in April 2023.