Security News

Threat hunters have discovered a new malware called Latrodectus that has been distributed as part of email phishing campaigns since at least late November 2023. "Latrodectus is an up-and-coming...

Hackers are using Facebook advertisements and hijacked pages to promote fake Artificial Intelligence services, such as MidJourney, OpenAI's SORA and ChatGPT-5, and DALL-E, to infect unsuspecting users with password-stealing malware. In one of the cases seen by researchers at Bitdefender, a malicious Facebook page impersonating Midjourney amassed 1.2 million followers and remained active for nearly a year before it was eventually taken down.
Bogus installers for Adobe Acrobat Reader are being used to distribute a new multi-functional malware dubbed Byakugan. The starting point of the attack is a PDF file written in Portuguese that,...

Financial organizations in the Asia-Pacific (APAC) and Middle East and North Africa (MENA) are being targeted by a new version of an "evolving threat" called JSOutProx. "JSOutProx is a...

A relatively new malware called Latrodectus is believed to be an evolution of the IcedID loader, seen in malicious email campaigns since November 2023. IcedID is a malware family first identified in 2017 that was originally classified as a modular banking trojan designed to steal financial information from infected computers.

Visa is warning about a spike in detections for a new version of the JsOutProx malware targeting financial institutions and their customers. In a security alert from Visa's Payment Fraud Disruption unit seen by BleepingComputer and sent to card issuers, processors, and acquirers, Visa says they became aware of a new phishing campaign distributing the remote access trojan on March 27, 2024.

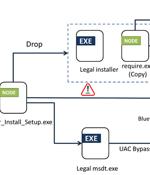
A suspected Vietnamese-origin threat actor has been observed targeting victims in several Asian and Southeast Asian countries with malware designed to harvest valuable data since at least May...

An updated version of an information-stealing malware called Rhadamanthys is being used in phishing campaigns targeting the oil and gas sector. "The phishing emails use a unique vehicle incident...

Today's malware is not just about causing immediate damage; some programs get embedded within systems to siphon off data over time, disrupt operations strategically, or lay the groundwork for massive, coordinated attacks. Read on to get the lowdown on recent high-profile malware attacks along with strategies to help limit malware risks at your organization.

The Chinese 'Winnti' hacking group was found using a previously undocumented malware called UNAPIMON to let malicous processes run without being detected. UNAPIMON is a C++ malware delivered in DLL form, which uses Microsoft Detours for hooking the CreateProcessW API function, allowing it to unhook critical API functions in child processes.