Security News

Finland's Transport and Communications Agency is warning about an ongoing Android malware campaign attempting to breach online bank accounts. The McAfee app is malware that will allow threat actors to breach victim's bank accounts.

The Iranian state-backed threat actor tracked as APT42 is employing social engineering attacks, including posing as journalists, to breach corporate networks and cloud environments of Western and Middle Eastern targets. Google threat analysts following APT42's operations report that the hackers use malicious emails to infect their targets with two custom backdoors, namely "Nicecurl" and "Tamecat," which provide command execution and data exfiltration capabilities.

Threat actors have been increasingly weaponizing Microsoft Graph API for malicious purposes with the aim of evading detection. This is done to "facilitate communications with command-and-control...

Cuttlefish, a new malware family that targets enterprise-grade small office/home office routers, is used by criminals to steal account credentials / secrets for AWS, CloudFlare, Docker, BitBucket, Alibaba Cloud and other cloud-based services. "With the stolen key material, the actor not only retrieves cloud resources associated with the targeted entity but gains a foothold into that cloud ecosystem," Black Lotus Labs researchers noted.
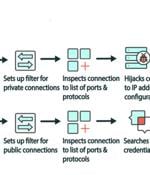
A new malware called Cuttlefish is targeting small office and home office (SOHO) routers with the goal of stealthily monitoring all traffic through the devices and gather authentication data from...

Cybersecurity researchers have discovered a previously undocumented malware targeting Android devices that uses compromised WordPress sites as relays for its actual command-and-control (C2)...

A new malware named 'Cuttlefish' has been spotted infecting enterprise-grade and small office/home office routers to monitor data that passes through them and steal authentication information. Lumen Technologies' Black Lotus Labs examined the new malware and reports that Cuttlefish creates a proxy or VPN tunnel on the compromised router to exfiltrate data discreetly while bypassing security measures that detect unusual sign-ins.

The authors behind the resurfaced ZLoader malware have added a feature that was originally present in the Zeus banking trojan that it's based on, indicating that it's being actively developed....

Latrodectus malware is now being distributed in phishing campaigns using Microsoft Azure and Cloudflare lures to appear legitimate while making it harder for email security platforms to detect the emails as malicious. Latrodectus is an increasingly distributed Windows malware downloader first discovered by Walmart's security team and later analyzed by ProofPoint and Team Cymru that acts as a backdoor, downloading additional EXE and DLL payloads or executing commands.

Three large-scale campaigns targeted Docker Hub users, planting millions of repositories that pushed malware and phishing sites since early 2021. As JFrog security researchers found, around 20% of the 15 million repositories hosted by Docker Hub contained malicious content, ranging from spam to dangerous malware and phishing sites.