Security News

Researchers are warning of threat actors increasingly abusing the Cloudflare Tunnel service in malware campaigns that usually deliver remote access trojans (RATs). [...]

Google has announced that it's adding a new layer of protection to its Chrome browser through what's called app-bound encryption to prevent information-stealing malware from grabbing cookies on Windows systems. "On Windows, Chrome uses the Data Protection API which protects the data at rest from other users on the system or cold boot attacks," Will Harris from the Chrome security team said.
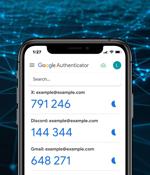
Google has fallen victim to its own ad platform, allowing threat actors to create fake Google Authenticator ads that push the DeerStealer information-stealing malware. [...]

Google says it's enhancing the security of sensitive data managed by Chrome for Windows users to fight the scourge of infostealer malware targeting cookies. Starting in Chrome 127, the stable version of which was released last week, the browser now uses app-bound encryption primitives that encrypt data in a way that links it to a specific app.

A new Android malware that researchers call 'BingoMod' can wipe devices after successfully stealing money from the victims' bank accounts using the on-device fraud technique. [...]

Zimperium's zLabs team has uncovered a new and widespread threat dubbed SMS Stealer. The SMS Stealer threat, first identified in 2022, uses fake ads and Telegram bots posing as legitimate services to trick victims into gaining access to their SMS messages.
The threat actors behind an ongoing malware campaign targeting software developers have demonstrated new malware and tactics, expanding their focus to include Windows, Linux, and macOS systems. DEV#POPPER is the moniker assigned to an active malware campaign that tricks software developers into downloading booby-trapped software hosted on GitHub under the guise of a job interview.

Japanese organizations are the target of a Chinese nation-state threat actor that leverages malware families like LODEINFO and NOOPDOOR to harvest sensitive information from compromised hosts while stealthily remaining under the radar in some cases for a time period ranging from two to three years. "The actors behind NOOPDOOR not only utilized LODEINFO during the campaign, but also utilized the new backdoor to exfiltrate data from compromised enterprise networks," it said.
A new malicious campaign has been observed making use of malicious Android apps to steal users' SMS messages since at least February 2022 as part of a large-scale campaign. Once installed, the app requests permission to access incoming SMS messages, following which it reaches out to one of the 13 command-and-control servers to transmit stolen SMS messages.

The Black Basta ransomware gang has shown resilience and an ability to adapt to a constantly shifting space, using new custom tools and tactics to evade detection and spread throughout a network. Black Basta is a ransomware operator who has been active since April 2022 and is responsible for over 500 successful attacks on companies worldwide.