Security News
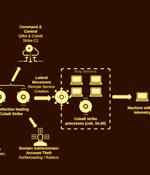
Companies based in the U.S. have been at the receiving end of an "Aggressive" Qakbot malware campaign that leads to Black Basta ransomware infections on compromised networks. "In this latest campaign, the Black Basta ransomware gang is using QakBot malware to create an initial point of entry and move laterally within an organization's network," Cybereason researchers Joakim Kandefelt and Danielle Frankel said in a report shared with The Hacker News.

Emsisoft's Black Friday through Cyber Monday deal is now live with 50% off Emsisoft Anti-Malware Home 1-year licenses for 1, 3, or 5 devices. Emsisoft is a powerful antivirus solution that uses a dual-scanning engine with definitions from both Emsisoft and Bitdefender.

As many as 34 Russian-speaking gangs distributing information-stealing malware under the stealer-as-a-service model stole no fewer than 50 million passwords in the first seven months of 2022. Aside from looting passwords, the stealers also harvested 2.11 billion cookie files, 113,204 crypto wallets, and 103,150 payment cards.

The operators of the Ducktail information stealer have demonstrated a "Relentless willingness to persist" and continued to update their malware as part of an ongoing financially driven campaign. "The malware is designed to steal browser cookies and take advantage of authenticated Facebook sessions to steal information from the victim's Facebook account," WithSecure researcher Mohammad Kazem Hassan Nejad said in a new analysis.

A malicious extension for Chromium-based web browsers has been observed to be distributed via a long-standing Windows information stealer called ViperSoftX. Czech-based cybersecurity company dubbed the rogue browser add-on VenomSoftX owing to its standalone features that enable it to access website visits, steal credentials and clipboard data, and even swap cryptocurrency addresses via an adversary-in-the-middle attack. The malware's use of a browser extension to advance its information-gathering goals was documented by Sophos threat analyst Colin Cowie earlier this year.

A new collection of malicious Android apps posing as harmless file managers had infiltrated the official Google Play app store, infecting users with the Sharkbot banking trojan. Because the trojan apps are file managers, it's less likely to raise suspicions when requesting dangerous permissions for loading the Sharkbot malware.

A nascent Go-based malware known as Aurora Stealer is being increasingly deployed as part of campaigns designed to steal sensitive information from compromised hosts. First advertised on Russian cybercrime forums in April 2022, Aurora was offered as a commodity malware for other threat actors, describing it as a "Multi-purpose botnet with stealing, downloading and remote access capabilities."

Cybercriminals are increasingly turning to a new Go-based information stealer named 'Aurora' to steal sensitive information from browsers and cryptocurrency apps, exfiltrate data directly from disks, and load additional payloads. According to cybersecurity firm SEKOIA, at least seven notable cybergangs with significant activity have adopted Aurora exclusively, or along with Redline and Raccoon, two other established information-stealing malware families.

The notorious Emotet malware has returned with renewed vigor as part of a high-volume malspam campaign designed to drop payloads like IcedID and Bumblebee. "Hundreds of thousands of emails per day" have been sent since early November 2022, enterprise security company Proofpoint said last week, adding, "The new activity suggests Emotet is returning to its full functionality acting as a delivery network for major malware families."

This Mark of the Web is an alternate data stream that contains information about the file, such as the URL security zone the file originates from, its referrer, and its download URL. When a user attempts to open a file with a MoTW attribute, Windows will display a security warning asking if they are sure they wish to open the file. After analyzing the files, Will Dormann, a senior vulnerability analyst at ANALYGENCE, discovered that the threat actors were using a new Windows zero-day vulnerability that prevented Mark of the Web security warnings from being displayed.