Security News

Apple rolled out patches on Good Friday to its iOS, iPadOS, and macOS operating systems and the Safari web browser to address vulnerabilities found by Google and Amnesty International that were exploited in the wild. The updates are to iOS 16.4.1, iPadOS 16.4.1, Safari 16.4.1, and macOS 13.3.1.

Apple on Friday released security updates for iOS, iPadOS, macOS, and Safari web browser to address a pair of zero-day flaws that are being exploited in the wild. Apple said it addressed CVE-2023-28205 with improved memory management and the second with better input validation, adding it's aware the bugs "May have been actively exploited."

A new info-stealing malware named MacStealer is targeting Mac users, stealing their credentials stored in the iCloud KeyChain and web browsers, cryptocurrency wallets, and potentially sensitive files. MacStealer is being distributed as a malware-as-a-service, where the developer sells premade builds for $100, allowing purchasers to spread the malware in their campaigns.
A new information-stealing malware has set its sights on Apple's macOS operating system to siphon sensitive information from compromised devices. First advertised on online hacking forums at the start of the month, it is still a work in progress, with the malware authors planning to add features to capture data from Apple's Safari browser and the Notes app.

On the first day of Pwn2Own Vancouver 2023, security researchers successfully demoed Tesla Model 3, Windows 11, and macOS zero-day exploits and exploit chains to win $375,000 and a Tesla Model 3. The STAR Labs team demoed a zero-day exploit chain targeting Microsoft's SharePoint team collaboration platform that brought them a $100,000 reward and successfully hacked Ubuntu Desktop with a previously known exploit for $15,000.

Mozilla has addressed issues causing Firefox to crash on macOS and to freeze with a non-responding blank window when starting on Windows 11 systems. According to the user who first reported the Windows freeze issue, the bug likely impacts Firefox users running Windows 11 who have also installed this month's KB5023706 cumulative update.
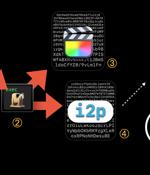
Trojanized versions of legitimate applications are being used to deploy evasive cryptocurrency mining malware on macOS systems. "This malware makes use of the Invisible Internet Project to download malicious components and send mined currency to the attacker's wallet," Jamf researchers Matt Benyo, Ferdous Saljooki, and Jaron Bradley said in a report shared with The Hacker News.

Apple this week released bug-splatting updates to its operating systems and Safari browser, to fix a zero-day vulnerability in its WebKit browser engine that's reported to have been actively exploited. Apple's advisory says the company "Is aware of a report that this issue may have been actively exploited." It credits an anonymous researcher for reporting the bug and its iOS advisory also acknowledges "The Citizen Lab at The University of Toronto's Munk School for their assistance."

Apple has released security updates that fix a WebKit zero-day vulnerability that "May have been actively exploited."The bug has been fixed in iOS 16.3.1 and iPadOS 16.3.1, macOS Ventura 13.2.1, Safari 16.3.1, and possibly also in tvOS 16.3.2 and watchOS 9.3.1 - though release notes for the updates for those Internet of Things operating systems have been temporarily witheld.

Apple on Monday rolled out security updates for iOS, iPadOS, macOS, and Safari to address a zero-day flaw that it said has been actively exploited in the wild. It's not immediately clear as to how the vulnerability is being exploited in real-world attacks, but it's the second actively abused type confusion flaw in WebKit to be patched by Apple after CVE-2022-42856 in as many months, which was closed in December 2022.