Security News

A new Mac malware named "Realst" is being used in a massive campaign targeting Apple computers, with some of its latest variants including support for macOS 14 Sonoma, which is still in development. The malware, first discovered by security researcher iamdeadlyz, is distributed to both Windows and macOS users in the form of fake blockchain games using names such as Brawl Earth, WildWorld, Dawnland, Destruction, Evolion, Pearl, Olymp of Reptiles, and SaintLegend.

Inventive attackers are specifically targeting Mac systems, as seen with the "Geacon" Cobalt Strike tool attack. To understand the state of cybersecurity on the Mac, the Moonlock team, a dedicated group of MacPaw's researchers and engineers focused on the cybersecurity needs of Mac users, conducted a survey.

Apple has released Rapid Security Response updates for iOS, iPadOS, macOS, and Safari web browser to address a zero-day flaw that it said has been actively exploited in the wild. The WebKit bug, cataloged as CVE-2023-37450, could allow threat actors to achieve arbitrary code execution when processing specially crafted web content.

How to Use an SSH Config File on macOS for Easier Connections to Your Data Center Servers Jack Wallen shows you how to make SSH connections even easier from your macOS machine. The only thing you'll need is a MacBook or iMac that includes SSH and some remote servers to connect to.

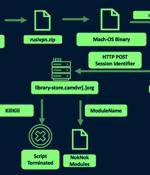
Security researchers observed a new campaign they attribute to the Charming Kitten APT group where hackers used new NokNok malware that targets macOS systems. After gaining the target's trust, Charming Kitten sends a malicious link that contains a Google Script macro, redirecting the victim to a Dropbox URL. This external source hosts a password-protected RAR archive with a malware dropper that leverages PowerShell code and an LNK file to stage the malware from a cloud hosting provider.
The Iranian nation-state actor known as TA453 has been linked to a new set of spear-phishing attacks that infect both Windows and macOS operating systems with malware. "TA453 eventually used a variety of cloud hosting providers to deliver a novel infection chain that deploys the newly identified PowerShell backdoor GorjolEcho," Proofpoint said in a new report.
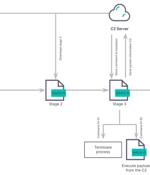
Researchers have pulled back the curtain on an updated version of an Apple macOS malware called Rustbucket that comes with improved capabilities to establish persistence and avoid detection by security software. "This variant of Rustbucket, a malware family that targets macOS systems, adds persistence capabilities not previously observed," Elastic Security Labs researchers said in a report published this week, adding it's "Leveraging a dynamic network infrastructure methodology for command-and-control."

Pub The command will print out your SSH key on your Linux machine without prompting you for your key authentication password. How to view your SSH public key on macOS. Viewing your keys on macOS can be done in a similar fashion as on Linux.

An unknown cryptocurrency exchange located in Japan was the target of a new attack earlier this month to deploy an Apple macOS backdoor called JokerSpy. Elastic Security Labs, which is monitoring the intrusion set under the name REF9134, said the attack led to the installation of Swiftbelt, a Swift-based enumeration tool inspired by an open-source utility called SeatBelt.

Apple on Wednesday released a slew of updates for iOS, iPadOS, macOS, watchOS, and Safari browser to address a set of flaws it said were actively exploited in the wild. The iPhone maker said it's aware that the two issues "May have been actively exploited against versions of iOS released before iOS 15.7," crediting Kaspersky researchers Georgy Kucherin, Leonid Bezvershenko, and Boris Larin for reporting them.