Security News

A Linux local privilege escalation flaw dubbed Dirty Pipe has been discovered and disclosed along with proof-of-concept exploit code. Max Kellermann said he found the programming blunder and reported it to the kernel security team in February, which issued patches within a few days.

A new Linux vulnerability known as 'Dirty Pipe' allows local users to gain root privileges through publicly available exploits. Security researcher Phith0n illustrated how they could use the exploit to modify the /etc/passwd file so that the root user does not have a password.
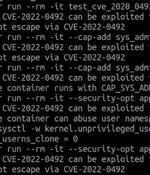
Details have emerged about a now-patched high-severity vulnerability in the Linux kernel that could potentially be abused to escape a container in order to execute arbitrary commands on the container host. The shortcoming resides in a Linux kernel feature called control groups, also referred to as cgroups version 1, which allows processes to be organized into hierarchical groups, effectively making it possible to limit and monitor the usage of resources such as CPU, memory, disk I/O, and network.

The Linux Foundation announced the final release of "Census II of Free and Open Source Software - Application Libraries," which identifies more than one thousand of the most widely deployed open source application libraries. This study informs what open source packages, components and projects warrant proactive operations and security support.

Kali Linux 2022.1 is your one-stop-shop for penetration testing. Offensive Security recently unleashed the first iteration of Kali Linux for 2022.

Pangu Lab's incident analysis involved three servers, one being the target of an external attack and two other internal machines - an email server and a business server. According to the researchers, the threat actor pivoted established a connection between the external server and the email server via a TCP SYN packet with a 264-byte payload. "At almost the same time, the [email] server connects to the [business] server's SMB service and performs some sensitive operations, including logging in to the [business] server with an administrator account, trying to open terminal services, enumerating directories, and executing Powershell scripts through scheduled tasks" - Pangu Lab.

Kali Linux 2022.1 released: New tools, kali-linux-everything, visual changesOffensive Security has released Kali Linux 2022.1, the latest version of its popular open source penetration testing platform. Attackers use Microsoft Teams as launchpad for malwareHackers are starting to realize that Microsoft Teams is a great means of spreading tentacles throughout an organization's systems; since the start of the year, Avanan has been seeing hackers increasingly dropping malware in Teams conversation.

The snap-confine tool in the Linux world's Snap software packaging system can be potentially exploited by ordinary users to gain root powers, says Qualys. Snap was developed by Ubuntu maker Canonical, and can be used with Ubuntu and on other Linux distributions, if one so wishes, to install applications and services.

Multiple security vulnerabilities have been disclosed in Canonical's Snap software packaging and deployment system, the most critical of which can be exploited to escalate privilege to gain root privileges. Snaps are self-contained application packages that are designed to work on operating systems that use the Linux kernel and can be installed using a tool called snapd.

Google says it bumped up rewards for reports of Linux Kernel, Kubernetes, Google Kubernetes Engine, or kCTF vulnerabilities by adding bigger bonuses for zero-day bugs and exploits using unique exploitation techniques. "We increased our rewards because we recognized that in order to attract the attention of the community we needed to match our rewards to their expectations," Google Vulnerability Matchmaker Eduardo Vela explained.