Security News

A critical security flaw has been disclosed in the Kubernetes Image Builder that, if successfully exploited, could be abused to gain root access under certain circumstances. The vulnerability,...

It's called leaving the door wide open – especially in Proxmox A critical bug in Kubernetes Image Builder could allow unauthorized SSH access to virtual machines (VMs) thanks to default...

A critical vulnerability in Kubernetes could allow unauthorized SSH access to a virtual machine running an image created with the Kubernetes Image Builder project. [...]

In this Help Net Security interview, Paolo Mainardi, CTO at SparkFabrik, discusses comprehensive strategies to secure Kubernetes environments from development through deployment. He focuses on...

Cybersecurity researchers have disclosed a security flaw impacting Microsoft Azure Kubernetes Services that, if successfully exploited, could allow an attacker to escalate their privileges and...

Portainer Community Edition is an open-source, lightweight service delivery platform for containerized applications. "I created Portainer, initially for my own needs. Back in 2016 I was operating a Public Cloud provider in Asia, and wanted to offer a Container as a Service solution to market. At the time, that meant Docker. There were no Cloud Provider management UI's for Docker then, so I created Portainer to act as such. In a way, Portainer enabled a domestic market version of AWS ECS before ECS was popular. However, Portainer quickly took on a life of its own. I open-sourced the UI, which was"discovered" and blogged about, and it took off.
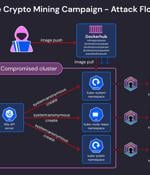
Cybersecurity researchers have warned of an ongoing cryptojacking campaign targeting misconfigured Kubernetes clusters to mine Dero cryptocurrency. Cloud security firm Wiz, which shed light on the...

Threat actors are actively exploiting critical vulnerabilities in OpenMetadata to gain unauthorized access to Kubernetes workloads and leverage them for cryptocurrency mining activity. That's...

In an ongoing Kubernetes cryptomining campaign, attackers target OpenMetadata workloads using critical remote code execution and authentication vulnerabilities. The security vulnerabilities exploited in these attacks were patched one month ago, on March 15, in OpenMedata versions 1.2.4 and 1.3.1.

Details have been made public about a now-patched high-severity flaw in Kubernetes that could allow a malicious attacker to achieve remote code execution with elevated privileges under specific...