Security News

South Korea has formally suspended new downloads of Chinese artificial intelligence (AI) chatbot DeepSeek in the country until the service makes changes to its mobile apps to comply with data...
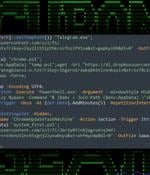
A nation-state threat actor with ties to North Korea has been linked to an ongoing campaign targeting South Korean business, government, and cryptocurrency sectors. The attack campaign, dubbed...

Yet another cash grab from Kim's cronies and an intel update from Microsoft North Korea has changed tack: its latest campaign targets the NPM registry and owners of Exodus and Atomic...

Remote position, webcam not working, then glitchy AI face ... Red alert! Twice, over the past two months, Dawid Moczadło has interviewed purported job seekers only to discover that these "software...

US, Japan, South Korea vow to intensify counter efforts North Korean blockchain bandits stole more than half a billion dollars in cryptocurrency in 2024 alone, the US, Japan, and South Korea say.…

North Korean state-backed hacking groups have stolen over $659 million worth of cryptocurrency in multiple crypto-heists, according to a joint statement issued by the United States, South Korea,...

DoJ thinks it's found the folks that ran it, and some of the 'IT warriors' sent out to fleece employers North Korea's fake IT worker scams netted the hermit kingdom $88 million over six years,...

South Korean police have arrested a CEO and five employees for manufacturing over 240,000 satellite receivers pre-loaded or later updated to include DDoS attack functionality at a purchaser's...

Evgenii Ptitsyn, a Russian national and suspected administrator of the Phobos ransomware operation, was extradited from South Korea and is facing cybercrime charges in the United States. [...]

10,000 of Kim Jong Un's soldiers believed to be headed for front line The EU has joined US and South Korean officials in expressing concern over a Russian transfer of technology to North Korea in...