Security News

Google has addressed a high-severity security flaw impacting the Android kernel that it has been actively exploited in the wild. That said, Clement Lecigne of Google's Threat Analysis Group has been credited with reporting the flaw, suggesting that it's likely being exploited by commercial spyware vendors to infiltrate Android devices in narrowly targeted attacks.


A novel Linux Kernel cross-cache attack named SLUBStick has a 99% success in converting a limited heap vulnerability into an arbitrary memory read-and-write capability, letting the researchers...

Redmond shared a technical incident response write-up on Saturday - titled "Windows Security best practices for integrating and managing security tools" - in which veep for enterprise and OS security David Weston explained how Microsoft measured the impact of the disaster: By accessing crash reports shared by customers. Weston's post justifies how Windows performed, on the grounds that kernel-level drivers - like those employed by CrowdStrike - can improve performance and prevent tampering with security software.

Microsoft has admitted that its estimate of 8.5 million machines crashed by CrowdStrike's faulty software update was almost certainly too low, and vowed to reduce infosec vendors' reliance on the kernel drivers at the heart of the issue. Redmond posted an incident response blog on Saturday - titled "Windows Security best practices for integrating and managing security tools" - in which veep for enterprise and OS security David Weston explained how Microsoft measured the impact of the incident: by accessing crash reports shared by customers.

Did the EU force Microsoft to let third parties like CrowdStrike run riot in the Windows kernel as a result of a 2009 undertaking? This is the implication being peddled by the Redmond-based cloud and software titan. As the tech industry deals with the fallout from the CrowdStrike incident, Microsoft is facing questions.

CrowdStrike's now-infamous Falcon Sensor software, which last week led to widespread outages of Windows-powered computers, has also caused crashes of Linux machines. A second issue titled "System crashed at cshook network ops inet6 sockraw release+0x171a9" advised users "For assistance with troubleshooting potential issues with the falcon lsm serviceable kernel module provided from the CrowdStrike Falcon Sensor/Agent security software suite." Red Hat also advised that "Disabling the CrowdStrike Falcon Sensor/Agent software suite will mitigate the crashes and provide temporary stability to the system in question while the issue is investigated." The issue was "Observed but not limited to release 6 and 7.".
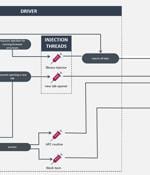
Cybersecurity researchers have shed light on an adware module that purports to block ads and malicious websites, while stealthily offloading a kernel driver component that grants attackers the ability to run arbitrary code with elevated permissions on Windows hosts. The malware, dubbed HotPage, gets its name from the eponymous installer, according to new findings from ESET. The installer "Deploys a driver capable of injecting code into remote processes, and two libraries capable of intercepting and tampering with browsers' network traffic," ESET researcher Romain Dumont said in a technical analysis published today.

Arm has issued a security bulletin warning of a memory-related vulnerability in Bifrost and Valhall GPU kernel drivers that is being exploited in the wild. The security issue is tracked as CVE-2024-4610 and is a use-after-free vulnerability that impacts all versions of Bifrost and Valhall drivers from r34p0 through r40p0.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a security flaw impacting the Linux kernel to the Known Exploited Vulnerabilities (KEV) catalog, citing evidence...