Security News

Malfunction took 14 plants offline for 36 hours. Oh, what a … nah, too obvious Toyota Japan has recovered from what it's described as a "malfunction in the production order system" that halted...

Japan's digital minister has doubled down on a June promise to penalize himself for the poor rollout of the country's digital ID, My Number Card, by offering up three months salary on Tuesday. The interim report reportedly revealed a lack of knowledge among the public on how to link their My Number Card to disability records, cases of health insurance being connected to the wrong card, and errors in pension records of public servants.

The NSA discovered the intrusion in 2020-we don't know how-and alerted the Japanese. The hackers had deep, persistent access and appeared to be after anything they could get their hands on-plans, capabilities, assessments of military shortcomings, according to three former senior U.S. officials, who were among a dozen current and former U.S. and Japanese officials interviewed, who spoke on the condition of anonymity because of the matter's sensitivity.

The port of Nagoya - which shifted 2.68 million shipping containers and 164 million tons of cargo in 2022 - has moved precious few in the last 24 hours after finding itself the latest victim of Russia's notorious LockBit ransomware gang. Japanese media have reported substantial disruptions at the port and named LockBit as the culprit.

The Port of Nagoya, the largest and busiest port in Japan, has been targeted in a ransomware attack that currently impacts the operation of container terminals.Today, the administrative authority of the Port of Nagoya has issued a notice about a malfunction in the "Nagoya Port Unified Terminal System" - the central system controlling all container terminals in the port.

Asia In Brief Japan's government last Friday rebuked Fujitsu for shabby cloud security. Fujitsu operates a cloud called "FENICS" and in February 2023 admitted that in December 2022 it had detected network misconfigurations that allowed unauthorized remote access to the service.

Fujitsu Japan is in the spotlight again for all the wrong reasons, after fumbling its attempt to fix the nation's troubled ID card scheme. One use of the cards is to arrange for administrative documents to be printed at convenience stores or government offices.

Japanese prime minister Fumio Kishida has ordered an emergency review of the nation's ID Cards, amid revelations of glitches and data leaks that threaten the government's digital services push. Japanese media reports that people with similar names are receiving cards intended for other people, while some recipients found the card links to records describing someone else.
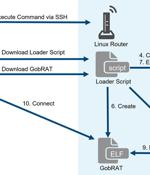
Linux routers in Japan are the target of a new Golang remote access trojan called GobRAT. "Initially, the attacker targets a router whose WEBUI is open to the public, executes scripts possibly by using vulnerabilities, and finally infects the GobRAT," the JPCERT Coordination Center said in a report published today. The compromise of an internet-exposed router is followed by the deployment of a loader script that acts as a conduit for delivering GobRAT, which, when launched, masquerades as the Apache daemon process to evade detection.

Japan's minister for digital transformation and digital reform, Tono Karo, has apologized after a government app breached citizens' privacy. Fujitsu Japan developed and operates the service, which preps PDF files in response to user requests and then despatches them to printers in convenience stores.