Security News

While Ivanti said the remote code execution risks are limited to "Certain conditions," the company didn't provide details on the vulnerable configurations. "We are not aware of any customers being exploited by these vulnerabilities at the time of disclosure," Ivanti added.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday placed three security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation....

Lynis: Open-source security auditing toolLynis is a comprehensive open-source security auditing tool for UNIX-based systems, including Linux, macOS, and BSD. WebCopilot: Open-source automation tool enumerates subdomains, detects bugsWebCopilot is an open-source automation tool that enumerates a target's subdomains and discovers bugs using various free tools. NIST's NVD has encountered a problemWhether the cause is insurmountable technical debt, lack of funds, a third reason or all of them, NIST's National Vulnerability Database is struggling, and it's affecting vulnerability management efforts.

Ivanti has disclosed details of a critical remote code execution flaw impacting Standalone Sentry, urging customers to apply the fixes immediately to stay protected against potential cyber...

Ivanti has fixed a critical RCE vulnerability in Ivanti Standalone Sentry that has been reported by researchers with the NATO Cyber Security Centre. The vulnerability affects all supported version of Ivanti Standalone Sentry as well as older, unsupported ones.

Ivanti warned customers to immediately patch a critical severity Standalone Sentry vulnerability reported by NATO Cyber Security Centre researchers. Ivanti also fixed a second critical vulnerability in its Neurons for ITSM IT service management solution that enables remote threat actors with access to an account with low privileges to execute commands "In the context of web application's user."

There's yet another group of miscreants out there hijacking insecure Ivanti devices: A new, financially motivated gang dubbed Magnet Goblin has emerged from the shadowy digital depths with a knack for rapidly exploiting newly disclosed vulnerabilities before vendors have issued a fix. The cybercrime crew has targeted US medical, manufacturing, and energy-sector organizations, according to Check Point, which said it spotted Magnet Goblin abusing security holes in Ivanti's code to break into networks back in January just one day after a proof-of-concept, or PoC, exploit was made public.
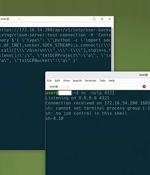
The Five Eyes (FVEY) intelligence alliance has issued a new cybersecurity advisory warning of cyber threat actors exploiting known security flaws in Ivanti Connect Secure and Ivanti Policy Secure...

The U.S. Cybersecurity and Infrastructure Security Agency revealed today that attackers who hack Ivanti VPN appliances using one of multiple actively exploited vulnerabilities may be able to maintain root persistence even after performing factory resets. The authoring organizations encourage network defenders to assume that user and service account credentials stored within the affected Ivanti VPN appliances are likely compromised, hunt for malicious activity on their networks using the detection methods and indicators of compromise within this advisory, run Ivanti's most recent external ICT, and apply available patching guidance provided by Ivanti as version updates become available.

The U.S. Cybersecurity and Infrastructure Security Agency revealed today that attackers who breached Ivanti appliances using one of multiple actively exploited vulnerabilities can maintain root persistence even after performing factory resets. CISA found that the Ivanti ICT failed to detect compromise while investigating multiple hacking incidents involving hacked Ivanti appliances.