Security News

An advanced persistent threat group, with ties to Iran, is believed behind a phishing campaign targeting high-profile government and military Israeli personnel, according to a report by Check Point Software. Targets of the campaign included a senior leadership in the Israeli defense industry, the former U.S. Ambassador to Israel and the former Deputy Prime Minister of Israel.

Microsoft on Thursday said it took steps to disable malicious activity stemming from abuse of OneDrive by a previously undocumented threat actor it tracks under the chemical element-themed moniker Polonium. In addition to removing the offending accounts created by the Lebanon-based activity group, the tech giant's Threat Intelligence Center said it suspended over 20 malicious OneDrive applications created and that it notified affected organizations.

Senior officials in the European Union were allegedly targeted with NSO Group's infamous Pegasus surveillance tool, according to a new report from Reuters. NSO Group said in a statement shared with Reuters that it was not responsible for the hacking attempts, adding that the targeting "Could not have happened with NSO's tools."

The Hamas-backed hacking group tracked as 'APT-C-23' was found catfishing Israeli officials working in defense, law, enforcement, and government agencies, ultimately leading to the deployment of new malware. According to analysts at Cybereason, who named this new campaign 'Operation Bearded Barbie,' APT-C-23 is also deploying new custom backdoors for Windows and Android devices geared towards espionage.
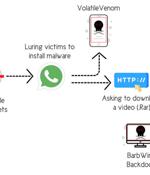
A threat actor with affiliations to the cyber warfare division of Hamas has been linked to an "Elaborate campaign" targeting high-profile Israeli individuals employed in sensitive defense, law enforcement, and emergency services organizations. "The campaign operators use sophisticated social engineering techniques, ultimately aimed to deliver previously undocumented backdoors for Windows and Android devices," cybersecurity company Cybereason said in a Wednesday report.

A prolific Middle East team with links to Hamas is said to be using malware and infrastructure to target high-ranking Israeli officials and steal sensitive data from Windows and Android devices. The advanced persistent threat group - known by some as APT-C-23, Arid Viper, Desert Falcon, and FrozenCell, among other names - set up an elaborate cyberespionage campaign, spending months rolling out fake Facebook accounts to target specific potential Israeli victims, according to Cybereason's Nocturnus threat intelligence team.

In this video for Help Net Security, Yonit Wiseman, Associate at YL Ventures, talks about the Israeli cybersecurity funding landscape in the past year. The Israeli cybersecurity industry has seen a rapid growth in the last decade, as many companies have reached the global market.

Israel's Nation Cyber Directorate confirmed in a tweet on Monday that a denial-of-service attack against a telecommunications provider took down several government sites, as well as others not affiliated with the government. Internet tracker NetBlocks reported that the attacks were launched against Israeli telecom providers Bezeq and Cellcom.

A massive distributed denial-of-service attack forced Israeli officials Monday to temporarily take down several government websites and to declare a state of online emergency to assess the damage and begin investigating who was behind the incident. In a tweet, the Israel National Cyber Directorate said it had detected the DDoS attack against a communications provider and that several websites had been taken down, though all have since resumed normal activity.

A number of websites belonging to the Israeli government were felled in a distributed denial-of-service attack on Monday, rendering the portals inaccessible for a short period of time. "In the past few hours, a DDoS attack against a communications provider was identified," the Israel National Cyber Directorate said in a tweet.