Security News
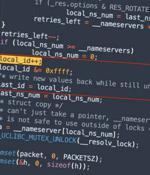
Cybersecurity researchers have disclosed an unpatched security vulnerability that could pose a serious risk to IoT products. The issue, which was originally reported in September 2021, affects the Domain Name System implementation of two popular C libraries called uClibc and uClibc-ng that are used for developing embedded Linux systems.

A new Mirai-based botnet malware named Enemybot has been observed growing its army of infected devices through vulnerabilities in modems, routers, and IoT devices, with the threat actor operating it known as Keksec. The particular threat group specializes in crypto-mining and DDoS; both supported by botnet malware that can nest in IoT devices and hijack their computational resources.

SentinelOne this week detailed a handful of bugs, including two critical remote code execution vulnerabilities, it found in Microsoft Azure Defender for IoT. These security flaws, which took six months to address, could have been exploited by an unauthenticated attacker to compromise devices and take over critical infrastructure networks. Microsoft Azure Defender for IoT is supposed to detect and respond to suspicious behavior as well as highlight known vulnerabilities, and manage patching and equipment inventories, for Internet-of-Things and industrial control systems.

Nearly half of businesses do not protect their full IoT suite. New research from Kaspersky indicates that 43% of businesses don't protect their full IoT business suite, leaving them vulnerable to cybersecurity breaches and data compromises.

The global IoT in manufacturing market is forecast to grow from $50 billion in 2021 to $87.9 billion by 2026, at a Compound Annual Growth Rate of 11.9% during the forecast period, according to ResearchAndMarkets. IoT in manufacturing is a technique of digital transformation that the manufacturing companies adopt for their efficient working of machines and their employees.

Mozilla fixes Firefox zero-days exploited in the wildMozilla has released an out-of-band security update for Firefox, Firefox Focus, and Thunderbird, fixing two critical vulnerabilities exploited by attackers in the wild. Easily exploitable Linux bug gives root access to attackersAn easily exploitable vulnerability in the Linux kernel can be used by local unprivileged users to gain root privileges on vulnerable systems by taking advantage of already public exploits.

As many as seven security vulnerabilities have been disclosed in PTC's Axeda software that could be weaponized to gain unauthorized access to medical and IoT devices. Collectively called "Access:7," the weaknesses - three of which are rated Critical in severity - potentially affect more than 150 device models spanning over 100 different manufacturers, posing a significant supply chain risk.

There are five key steps OEMs can take to reduce the complexity of security and the time and cost involved in building the right protection into their device(s), from the ground up. A threat model and security analysis is the next step on your security journey and it helps you establish your audit trail of best practice.

A set of seven vulnerabilities collectively tracked as Access:7 have been found in PTC's Axeda agent, a solution used for remote access and management of over 150 connected devices from more than 100 vendors. Developed by Parametric Technology Corporation, the Axeda platform through locally deployed agents provides telemetry data from IoT devices on the network and the option for remote service.

The global 5G IoT market size was valued at $1.4 billion in 2020 and is projected to reach $111.2 billion by 2028, growing at a CAGR of 72.1% from 2021 to 2028, according to Verified Market Research. Rising demand for IoT connected devices, more adoption of mobile broadband as well as a growing device-to-device communication, and swift innovation virtualization in the networking domain is driving the growth of the 5G Technology Market.