Security News

Cybersecurity company SentinelOne has revealed that a China-nexus threat cluster dubbed PurpleHaze conducted reconnaissance attempts against its infrastructure and some of its high-value...
Cybersecurity researchers are warning of continued risks posed by a distributed denial-of-service (DDoS) malware known as XorDDoS, with 71.3 percent of the attacks between November 2023 and...

PLUS: India's new electronics subsidies; Philippines unplugs a mobile carrier; Alibaba Cloud expands Asia In Brief Chinese officials admitted to directing cyberattacks on US infrastructure at a...

In this Help Net Security video, Ev Kontsevoy, CEO at Teleport, explores the risks AI agents pose to computing infrastructure, particularly when exposed to social engineering attacks. Unlike...
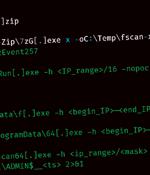
Threat hunters have uncovered a new threat actor named UAT-5918 that has been attacking critical infrastructure entities in Taiwan since at least 2023. "UAT-5918, a threat actor believed to be...

CISA says the Medusa ransomware operation has impacted over 300 organizations in critical infrastructure sectors in the United States until last month. [...]

The US Justice Department has charged Chinese state security officers along with APT27 and i-Soon hackers for network breaches and cyberattacks that have targeted victims globally since 2011. [...]

Why Digital Trust and crypto-agility are essential to authentication and data security Sponsored Post Research firm IDC estimates that over 53 percent of organizations are now mostly or completely...

IOCONTROL targets IoT and OT devices from a ton of makers, apparently An Iranian government-linked cybercriminal crew used custom malware called IOCONTROL to attack and remotely control US and...

Iranian threat actors are utilizing a new malware named IOCONTROL to compromise Internet of Things (IoT) devices and OT/SCADA systems used by critical infrastructure in Israel and the United States. [...]