Security News

As part of this partnership, Liquid Web customers can employ the Threat Stack Oversight Intrusion Detection System as an additional layer of security to Liquid Web servers with an advanced Intrusion Detection System. Together, Threat Stack Oversight and Liquid Web will provide customers with real-time monitoring for user, process, network, and file behaviors in critical systems across Linux and Windows servers.

This cloud-based software offers a simple, secure, adaptable and efficient way to issue physical and digital IDs using a single, easy-to-use platform. As organizations become more decentralized, opening the door to new requirements to securely manage and remotely issue credentials, there is an increase in pressure to maintain a safe and secure flow of data - including the data stored on physical and digital credentials.

Finland's domestic security agency said Thursday that the cybergroup APT31, which is generally linked to the Chinese government, was likely behind a cyberspying attack on the information systems of the Nordic country's parliament. The Finnish Security and Intelligence Service, known by the abbreviation Supo, said it had "Identified a cyber espionage operation targeted in 2020 against parliament with the aim of intruding into parliament's IT systems."

Government imposter scams now come with a new twist that has the potential to make them even more effective, as the Inspector General for the Social Security Administration warns. According to reports received by the Office of the Inspector General, the scammers' tactics arsenal has been updated to include the use of fake IDs designed to look like those used by Federal employees.

A publicly exposed cloud storage bucket was found to contain images of hundreds of passports and identity documents belonging to journalists and volleyball players from around the world. Reverse-image searches for headshots revealed that these well-known European volleyball players were either directly associated with CEV or were part of a volleyball team or federation affiliated with the CEV. BleepingComputer also found some of CEV's assets in the bucket, such as branding images with CEV logos on them.

A vulnerability in the popular TikTok short-form video-sharing platform could have allowed attackers to easily compile users' phone numbers, unique user IDs and other data ripe for phishing attacks. In order to help users find friends through their contacts, TikTok contained a sync feature for contacts who had TikTok accounts.

Its intrusion detection and prevention system feature on its gateway hardware fetched a set of rules from an outside source that were broken, and rather than ignore the invalid data and fall back to known-valid data, it simply silently stopped working. What should have happened is that Ubiquiti should have validated the rules before passing them to customer equipment, and the firmware on the gadgets should not have thrown away its previous rules before installing, and failing on, the latest ones.

Stamus Networks announced the general availability of SELKS 6 - the turnkey system based on Suricata intrusion detection/prevention and network security monitoring with a network threat hunting interface and graphical rule manager. "We are excited to make SELKS 6 officially available," said Peter Manev, co-founder and chief strategy officer of Stamus Networks.
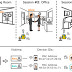
Researchers have uncovered a potential means to profile and track online users using a novel approach that combines device identifiers with their biometric information. The details come from a newly published research titled "Nowhere to Hide: Cross-modal Identity Leakage between Biometrics and Devices" by a group of academics from the University of Liverpool, New York University, The Chinese University of Hong Kong, and University at Buffalo SUNY. "Prior studies on identity theft only consider the attack goal for a single type of identity, either for device IDs or biometrics," Chris Xiaoxuan Lu, Assistant Professor at the University of Liverpool, told The Hacker News in an email interview.

Researchers have uncovered a potential means to profile and track online users using a novel approach that combines device identifiers with their biometric information. The details come from a newly published research titled "Nowhere to Hide: Cross-modal Identity Leakage between Biometrics and Devices" by a group of academics from the University of Liverpool, New York University, The Chinese University of Hong Kong, and University at Buffalo SUNY. "Prior studies on identity theft only consider the attack goal for a single type of identity, either for device IDs or biometrics," Chris Xiaoxuan Lu, Assistant Professor at the University of Liverpool, told The Hacker News in an email interview.