Security News
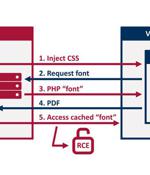
Researchers have disclosed an unpatched security vulnerability in "Dompdf," a PHP-based HTML to PDF converter, that, if successfully exploited, could lead to remote code execution in certain configurations. In other words, the flaw allows a malicious party to upload font files with a.php extension to the web server, which can then be activated by using an XSS vulnerability to inject HTML into a web page before it's rendered as a PDF. This meant that the attacker could potentially navigate to the uploaded.
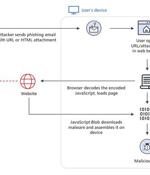
Threat actors are increasingly banking on the technique of HTML smuggling in phishing campaigns as a means to gain initial access and deploy an array of threats, including banking malware, remote administration trojans, and ransomware payloads. HTML smuggling is an approach that allows an attacker to "Smuggle" first-stage droppers, often encoded malicious scripts embedded within specially-crafted HTML attachment or web pages, on a victim machine by taking advantage of basic features in HTML5 and JavaScript rather than exploiting a vulnerability or a design flaw in modern web browsers.

Microsoft has seen a surge in malware campaigns using HTML smuggling to distribute banking malware and remote access trojans. While HTML smuggling is not a new technique, Microsoft is seeing it increasingly used by threat actors to evade detection, including the Nobelium hacking group behind the SolarWinds attacks.

Menlo shared the news along with its discovery of an HTML smuggling campaign it named ISOMorph, which uses the same technique the SolarWinds attackers used in their most recent spearphishing campaign. The ISOMorph attack uses HTML smuggling to drop its first stage on a victim's computer.

Turns out, all it takes for attackers to alter the "External sender" warning, or remove it altogether from emails is just a few lines of HTML and CSS code. Email security products such as enterprise email gateways are often configured to display the "External sender" warning to a recipient when an email arrives from outside of the organization.

A recent phishing campaign used a clever trick to deliver the fraudulent web page that collects Microsoft Office 365 credentials by building it from chunks of HTML code stored locally and remotely. The method consists of gluing together multiple pieces of HTML hidden in JavaScript files to obtain the fake login interface and prompt the potential victim to type in the sensitive information.

An ongoing cybercrime campaign is employing a technique known as HTML smuggling to deliver malware onto the victim's machine, Menlo Security reports. Referred to as Duri, the campaign started in early July and continues to date, attempting to evade network security solutions, including proxies and sandboxes, to deliver malicious code.

An active campaign has been spotted that utilizes HTML smuggling to deliver malware, effectively bypassing various network security solutions, including sandboxes, legacy proxies and firewalls. Krishnan Subramanian, security researcher with Menlo Security, told Threatpost that the campaign uncovered on Tuesday, dubbed "Duri," has been ongoing since July.

Except for phishing and scams, downloading an HTML attachment and opening it locally on your browser was never considered as a severe threat until a security researcher today demonstrated a...

A new type of DDoS attack that abuses the HTML5 Ping-based hyperlink auditing feature has been detected following a major attack emanating from primarily Chinese-speaking mobile users of the...