Security News
A threat actor with affiliations to the cyber warfare division of Hamas has been linked to an "Elaborate campaign" targeting high-profile Israeli individuals employed in sensitive defense, law enforcement, and emergency services organizations. "The campaign operators use sophisticated social engineering techniques, ultimately aimed to deliver previously undocumented backdoors for Windows and Android devices," cybersecurity company Cybereason said in a Wednesday report.

A prolific Middle East team with links to Hamas is said to be using malware and infrastructure to target high-ranking Israeli officials and steal sensitive data from Windows and Android devices. The advanced persistent threat group - known by some as APT-C-23, Arid Viper, Desert Falcon, and FrozenCell, among other names - set up an elaborate cyberespionage campaign, spending months rolling out fake Facebook accounts to target specific potential Israeli victims, according to Cybereason's Nocturnus threat intelligence team.

Israel said Thursday it will begin seizing cryptocurrency accounts used by the Palestinian Hamas group to raise money for its armed wing. Israeli Defense Minister Benny Gantz ordered security forces to seize the accounts after a joint operation "Uncovered a web of electronic wallets" used by Hamas to raise funds using bitcoin and other cryptocurrencies, the ministry said.

The Israeli Air Force has claimed that in the past week its fighter jets bombed two buildings allegedly used by the cyber unit of Hamas, the Palestinian militant group that runs Gaza. The first announcement was made on May 14, when Israel announced a strike on what it described as a "Cyber-equipment storage site of the Hamas terror organization cyber unit." The Air Force said the building was located in the northern Gaza Strip and it belonged to Hamas military intelligence.

In October 2020, KrebsOnSecurity looked at how a web of sites connected to conspiracy theory movements QAnon and 8chan were being kept online by DDoS-Guard, a dodgy Russian firm that also hosts the official site for the terrorist group Hamas. New research shows DDoS-Guard relies on data centers provided by a U.S.-based publicly traded company, which experts say could be exposed to civil and criminal liabilities as a result of DDoS-Guard's business with Hamas.

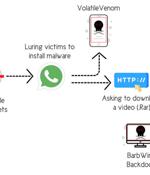
Two new backdoors have been attributed to the Molerats advanced persistent threat group, which is believed to be associated with the Palestinian terrorist organization Hamas. In early 2020, security researchers at Cybereason's Nocturnus group published information on two new malware families used by the APT, namely Spark and Pierogi.

MoleRATs, a politically-motivated threat actor apparently linked to the Palestinian terrorist organization Hamas, has expanded its target list to include insurance and retail industries, Palo Alto Networks' security researchers report. Spear-phishing emails were leveraged to deliver malicious documents - mostly Word documents, but also one PDF - which in turn attempted to trick the intended victim into enabling content to run a macro, or force them into clicking a link to download a malicious payload. The Spark backdoor was used in most of these assaults, allowing the attackers to open applications and run command line commands on the compromised system.

Hamas has been caught taking a classic "Catfish" approach, to tempt Israeli soldiers into installing spyware on their phones. The IDF told the Times of Israel that the idea was to catch male targets' attention, strike up a rapport and eventually lure the soldiers into installing a special app on their phones.

JERUSALEM - The Israeli military on Sunday said it has thwarted an attempt by the Hamas militant group to hack soldiers' phones by posing as young, attractive women on social media, striking up friendships and persuading them into downloading malware. Jonathan Conricus told reporters that the phones of dozens of soldiers had been infected in recent months, although he said the army detected the scam early on and prevented any major secrets from reaching the Islamic militant group.

Quick-fire summary of the past few days of news Roundup Welcome back, Brits, from your three-day Bank Holiday week. Allow us to catch you up on recent infosec comings and goings.…