Security News

The Chinese Cicada hacking group, tracked as APT10, was observed abusing security software to install a new version of the LODEINFO malware against Japanese organizations. The cybersecurity company has published two reports, one illustrating new APT10's infection chain techniques and a second focusing on the evolution of LODEINFO. Abusing security software.

In this interview for Help Net Security, James Turgal, VP of Cyber Risk, Strategy and Board Relations at Optiv, talks about election cybersecurity and how to keep elections and electoral campaigns safe. After the results of the most recent presidential election was almost overshadowed by so-called "Election deniers" and those who continue to claim fraud in the votes cast, all eyes are on the midterm elections in November.

A new version of the 'FurBall' Android spyware has been found targeting Iranian citizens in mobile surveillance campaigns conducted by the Domestic Kitten hacking group, also known as APT-C-50. The newest FurBall malware version was sampled and analyzed by ESET researchers, who report it has many similarities with earlier versions, but now comes with obfuscation and C2 updates.

The Federal Police of Brazil on Wednesday announced it had arrested an individual for purported links to the notorious LAPSUS$ extortionist gang. Other federal government portals targeted by the LAPSUS$ group in Brazil include the Ministry of Economy, Comptroller General of the Union, and the Federal Highway Police.

Today, the Brazilian Federal Police arrested a Brazilian suspect in Feira de Santana, Bahia, believed to be part of the Lapsus$ extortion gang. The suspect was detained following an investigation started in December 2021 after last year's breach of the Brazilian Ministry of Health.
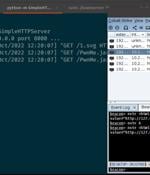
HelpSystems, the company behind the Cobalt Strike software platform, has released an out-of-band security update to address a remote code execution vulnerability that could allow an attacker to take control of targeted systems. Cobalt Strike is a commercial red-team framework that's mainly used for adversary simulation, but cracked versions of the software have been actively abused by ransomware operators and espionage-focused advanced persistent threat groups alike.

The criminals targeted vehicles with keyless entry and start systems, exploiting the technology to get into the car and drive away. A total of 22 locations were searched, and over EUR 1 098 500 in criminal assets seized.

On Thursday, a Puerto Rico judge sentenced a former University of Puerto Rico student to 13 months in prison for hacking over a dozen email and Snapchat accounts of female colleagues. Besides targeting dozens of student email accounts, he successfully hacked into multiple university email accounts and collected personal information in spoofing and phishing attacks.

Unfortunately the page that you requested does not exist. Don't worry we have some great suggestions to help you on your way! Based on the keywords found in the URL that you attempted to visit, we have suggested similar content and articles below.

The Cheerscrypt ransomware has been linked to a Chinese hacking group named 'Emperor Dragonfly,' known to frequently switch between ransomware families to evade attribution. The ransomware gang is tracked under different names, such as Bronze Starlight and DEV-0401, and has been seen using a wide variety of ransomware families since 2021.