Security News

The police in Spain have arrested José Luis Huertas, a 19-year-old regarded as the most dangerous hackers in the country. A police investigation started in November 2022 eventually lead to the identification and arrest of the young hacker, who has been described as "a serious threat to national security."

Unknown threat actors are actively exploiting a recently patched security vulnerability in the Elementor Pro website builder plugin for WordPress. The premium plugin is estimated to be used on over 12 million sites.

Hackers are actively exploiting a high-severity vulnerability in the popular Elementor Pro WordPress plugin used by over eleven million websites. Elementor Pro is a WordPress page builder plugin allowing users to easily build professional-looking sites without knowing how to code, featuring drag and drop, theme building, a template collection, custom widget support, and a WooCommerce builder for online shops.

A Russian hacking group tracked as TA473, aka 'Winter Vivern,' has been actively exploiting vulnerabilities in unpatched Zimbra endpoints since February 2023 to steal the emails of NATO officials, governments, military personnel, and diplomats. Today, Proofpoint has published a new report on how the threat actor exploits CVE-2022-27926 on Zimbra Collaboration servers to access the communications of NATO-aligned organizations and persons.

A digitally signed and trojanized version of the 3CX Voice Over Internet Protocol desktop client is reportedly being used to target the company's customers in an ongoing supply chain attack. 3CX is a VoIP IPBX software development company whose 3CX Phone System is used by more than 600,000 companies worldwide and has over 12 million daily users.

Pwn2Own Vancouver 2023 has ended with contestants earning $1,035,000 and a Tesla Model 3 car for 27 zero-day exploited between March 22 and 24. The total prize pool for Pwn2Own Vancouver 2023 was over $1,000,000 in cash and a Tesla Model 3, which Team Synacktiv won.

In brief A team of hackers from French security shop Synacktiv have won $100,000 and a Tesla Model 3 after subverting the Muskmobile's entertainment system, and from there opening up the car's core management systems. In the US, the Office of Inspector General of General Services Administration, issued a redacted report [PDF] earlier this month that found the government agency had misled its customers and other government agencies by telling them that Login.
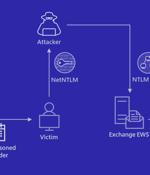
Microsoft on Friday shared guidance to help customers discover indicators of compromise associated with a recently patched Outlook vulnerability.Tracked as CVE-2023-23397, the critical flaw relates to a case of privilege escalation that could be exploited to steal NT Lan Manager hashes and stage a relay attack without requiring any user interaction.

Its ranking hovers between 1,500 and 2,000 on Amazon. For those of you in New York, I'm giving at book talk at the Ford Foundation on Thursday, April 6.

A cyberespionage hacking group tracked as 'Bitter APT' was recently seen targeting the Chinese nuclear energy industry using phishing emails to infect devices with malware downloaders. Bitter is a suspected South Asian hacking group known to target high-profile organizations in the energy, engineering, and government sectors in the Asian-Pacific region.