Security News
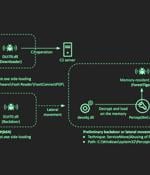
The North Korean threat actor known as the Lazarus Group has been observed shifting its focus and rapidly evolving its tools and tactics as part of a long-running activity called DeathNote. The targeting of the automotive and academic verticals is tied to Lazarus Group's broader attacks against the defense industry, as documented by the Russian cybersecurity firm in October 2021, leading to the deployment of BLINDINGCAN and COPPERHEDGE implants.

Enterprise communications service provider 3CX confirmed that the supply chain attack targeting its desktop application for Windows and macOS was the handiwork of a threat actor with North Korean nexus. It's worth noting that cybersecurity firm CrowdStrike has attributed the attack to a Lazarus sub-group dubbed Labyrinth Chollima, citing tactical overlaps.

VoIP communications company 3CX confirmed today that a North Korean hacking group was behind last month's supply chain attack. "Based on the Mandiant investigation into the 3CX intrusion and supply chain attack thus far, they attribute the activity to a cluster named UNC4736. Mandiant assesses with high confidence that UNC4736 has a North Korean nexus," 3CX CISO Pierre Jourdan said today.
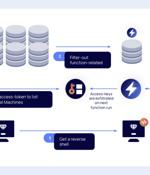
A "By-design flaw" uncovered in Microsoft Azure could be exploited by attackers to gain access to storage accounts, move laterally in the environment, and even execute remote code. "It is possible to abuse and leverage Microsoft Storage Accounts by manipulating Azure Functions to steal access-tokens of higher privilege identities, move laterally, potentially access critical business assets, and execute remote code," Orca said in a new report shared with The Hacker News.

Threat actors are flooding the npm open source package repository with bogus packages that briefly even resulted in a denial-of-service attack. "The threat actors create malicious websites and publish empty packages with links to those malicious websites, taking advantage of open-source ecosystems' good reputation on search engines," Checkmarx's Jossef Harush Kadouri said in a report published last week.

The Iranian nation-state group known as MuddyWater has been observed carrying out destructive attacks on hybrid environments under the guise of a ransomware operation. That's according to new findings from the Microsoft Threat Intelligence team, which discovered the threat actor targeting both on-premises and cloud infrastructures in partnership with another emerging activity cluster dubbed DEV-1084.

Security researchers discovered a new malicious browser extension called Rilide, that targets Chromium-based products like Google Chrome, Brave, Opera, and Microsoft Edge. Researchers at Trustwave SpiderLabs found that Rilide mimicked benign Google Drive extensions to hide in plain sight while abusing built-in Chrome functionalities.

Spanish cops have arrested a 19-year-old suspected of stealing records belonging to half a million taxpayers and developing a database to sell stolen information to other cyber criminals. José Luis Huertas, better known as Alcasec, has been described as the "Robin Hood hacker" and a "Dangerous computer criminal."

Multiple vulnerabilities discovered Nexx smart devices can be exploited to control garage doors, disable home alarms, or smart plugs. The most significant discovery is the use of universal credentials that are hardcoded in the firmware and also easy to obtain from the client communication with Nexx's API. The vulnerability can also be exploited to identify Nexx users, allowing an attacker to collect email addresses, device IDs, and first names.
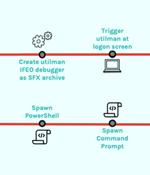
An unknown threat actor used a malicious self-extracting archive file in an attempt to establish persistent backdoor access to a victim's environment, new findings from CrowdStrike show. SFX files are capable of extracting the data contained within them without the need for dedicated software to display the file contents.