Security News

Six sites targeted for security clean-up, just 49,994 to go A plan for hackers to help secure America's critical infrastructure has kicked off with six US water companies signing up to let coders...

A new malicious campaign is using a legitimate but old and vulnerable Avast Anti-Rootkit driver to evade detection and take control of the target system by disabling security components. [...]
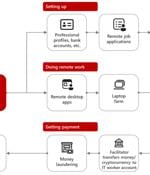
The North Korea-linked threat actor known as Sapphire Sleet is estimated to have stolen more than $10 million worth of cryptocurrency as part of social engineering campaigns orchestrated over a...

Russian state hackers APT28 (Fancy Bear/Forest Blizzard/Sofacy) breached a U.S. company through its enterprise WiFi network while being thousands of miles away, by leveraging a novel technique...

Threat actors with ties to Russia have been linked to a cyber espionage campaign aimed at organizations in Central Asia, East Asia, and Europe. Recorded Future's Insikt Group, which has assigned...

A new Linux backdoor called 'WolfsBane' has been discovered, believed to be a port of Windows malware used by the Chinese 'Gelsemium' hacking group. [...]

Threat actors are increasingly banking on a new technique that leverages near-field communication (NFC) to cash out victim's funds at scale. The technique, codenamed Ghost Tap by ThreatFabric,...

A new China-linked cyber espionage group has been attributed as behind a series of targeted cyber attacks targeting telecommunications entities in South Asia and Africa since at least 2020 with...

Malicious actors are exploiting misconfigured JupyterLab and Jupyter Notebooks to conduct stream ripping and enable sports piracy using live streaming capture tools. The attacks involve the hijack...

U.S. telecoms giant T-Mobile has confirmed that it was also among the companies that were targeted by Chinese threat actors to gain access to valuable information. The adversaries, tracked as Salt...