Security News

At least three different advanced persistent threat groups from across the world have launched spear-phishing campaigns in mid-March 2022 using the ongoing Russo-Ukrainian war as a lure to distribute malware and steal sensitive information. "Many of these lure documents utilize malicious macros or template injection to gain an initial foothold into the targeted organizations, and then launch malware attacks."

An Android spyware application has been spotted masquerading as a "Process Manager" service to stealthily siphon sensitive information stored in the infected devices. "When the application is run, a warning appears about the permissions granted to the application," Lab52 researchers said.

Email marketing firm MailChimp disclosed on Sunday that they had been hit by hackers who gained access to internal customer support and account management tools to steal audience data and conduct phishing attacks. In an email to BleepingComputer, MailChimp has confirmed that the breach was more significant than just Trezor's account being accessed by threat actors.

A rich new set of FIN7 indicators of compromise based on the analysis of novel malware samples has been published by researchers at Mandiant, who continue to observe and track the group's operations. In some intrusions, FIN7 was observed tweaking the functionality and adding new features to PowerPlant, and deploying the new version in the middle of the operation.

The City of London Police on Friday disclosed that it has charged two of the seven teenagers, a 16-year-old and a 17-year-old, who were arrested last week for their alleged connections to the LAPSUS$ data extortion gang. "Both teenagers have been charged with: three counts of unauthorized access to a computer with intent to impair the reliability of data; one count of fraud by false representation and one count of unauthorized access to a computer with intent to hinder access to data," Detective Inspector Michael O'Sullivan, from the City of London Police, said in a statement.
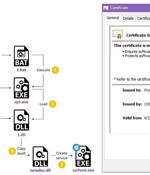
A Chinese advanced persistent threat tracked as Deep Panda has been observed exploiting the Log4Shell vulnerability in VMware Horizon servers to deploy a backdoor and a novel rootkit on infected machines with the goal of stealing sensitive data. Cybersecurity firm CrowdStrike, which assigned the panda-themed name to the group all the way back in July 2014, called it "One of the most advanced Chinese nation-state cyber intrusion groups."

Two new security vulnerabilities have been disclosed in Rockwell Automation's programmable logic controllers and engineering workstation software that could be exploited by an attacker to inject malicious code on affected systems and stealthily modify automation processes. CVE-2022-1161 - A remotely exploitable flaw that allows a malicious actor to write user-readable "Textual" program code to a separate memory location from the executed compiled code.
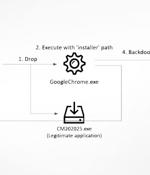
The North Korean state-backed hacking crew, otherwise known as the Lazarus Group, has been attributed to yet another financially motivated campaign that leverages a trojanized decentralized finance wallet app to distribute a fully-featured backdoor onto compromised Windows systems. The app, which is equipped with functionalities to save and manage a cryptocurrency wallet, is also designed to trigger the launch of the implant that can take control of the infected host.

Apple and Meta shared data with child hackers pretending to be law enforcement. It was revealed on March 30 that both Apple and Facebook parent company, Meta, were duped by child hackers impersonating law enforcement officers last year, according to a report from Bloomberg.

A new information-stealing malware named BlackGuard is winning the attention of the cybercrime community, now sold on numerous darknet markets and forums for a lifetime price of $700 or a subscription of $200 per month. BlackGuard's evasion capabilities are still under heavy development, but some systems are already in place to help the malware escape detection and analysis.