Security News

Multiple cybersecurity and law enforcement agencies from FVEY countries shared guidance for MSPs to secure networks and sensitive data against these rising cyber threats. "The UK, Australian, Canadian, New Zealand, and U.S. cybersecurity authorities expect malicious cyber actors-including state-sponsored advanced persistent threat groups-to step up their targeting of MSPs in their efforts to exploit provider-customer network trust relationships," the joint advisory reads.

Hackers have carried out over 65,000 attacks through Windows' Print Spooler exploit. A new report, from cybersecurity company Kaspersky, has found that cybercriminals conducted approximately 65,000 attacks through Windows' Print Spooler application between July 2021 and April 2022.

Threat actors have started exploiting a critical bug in the application service provider F5's BIG-IP modules after a working exploit of the vulnerability was publicly made available. A shodan query shared by security researcher Jacob Baines revealed thousands of exposed BIG-IP systems on the internet, which an attacker can leverage to exploit remotely.

Hackers continue to target Russia with cyberattacks, defacing Russian TV to show pro-Ukrainian messages and taking down the RuTube video streaming site. During the Russian President Putin's speech at today's "Victory Day" military parade, pro-Ukrainian hacking groups defaced the online Russian TV schedule page to display anti-war messages.

Threat actors have started massively exploiting the critical vulnerability tracked as CVE-2022-1388, which affects multiple versions of all F5 BIG-IP modules, to drop malicious payloads. F5 last week released patches for the security issue, which affects the BIG-IP iControl REST authentication component.

Threat actors have started massively exploiting the critical vulnerability tracked as CVE-2022-1388, which affects multiple versions of all F5 BIG-IP modules, to drop malicious payloads. F5 last week released patches for the security issue, which affects the BIG-IP iControl REST authentication component.

Security researchers have noticed a malicious campaign that used Windows event logs to store malware, a technique that has not been previously documented publicly for attacks in the wild. The method enabled the threat actor behind the attack to plant fileless malware in the file system in an attack filled with techniques and modules designed to keep the activity as stealthy as possible.

The U.S. State Department has announced rewards of up to $10 million for any information leading to the identification of key individuals who are part of the infamous Conti cybercrime gang. It's offering another $5 million for intelligence information that could help arrest or convict individuals who are conspiring or attempting to affiliate with the group in a ransomware attack.
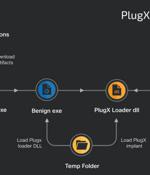
The China-based threat actor known as Mustang Panda has been observed refining and retooling its tactics and malware to strike entities located in Asia, the European Union, Russia, and the U.S. "Mustang Panda is a highly motivated APT group relying primarily on the use of topical lures and social engineering to trick victims into infecting themselves," Cisco Talos said in a new report detailing the group's evolving modus operandi. The group is known to have targeted a wide range of organizations since at least 2012, with the actor primarily relying on email-based social engineering to gain initial access to drop PlugX, a backdoor predominantly deployed for long-term access.
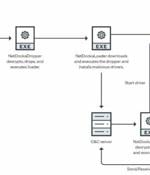
A pay-per-install malware service known as PrivateLoader has been spotted distributing a "Fairly sophisticated" framework called NetDooka, granting attackers complete control over the infected devices. PrivateLoader, as documented by Intel 471 in February 2022, functions as a downloader responsible for downloading and installing additional malware onto the infected system, including SmokeLoader, RedLine Stealer, Vidar, Raccoon, GCleaner, and Anubis.