Security News
The cyber espionage group known as Bahamut has been attributed as behind a highly targeted campaign that infects users of Android devices with malicious apps designed to extract sensitive information. The activity, which has been active since January 2022, entails distributing rogue VPN apps through a fake SecureVPN website set up for this purpose, Slovak cybersecurity firm ESET said in a new report shared with The Hacker News.

A cybercriminal operation tracked as Ducktail has been hijacking Facebook Business accounts causing losses of up to $600,000 in advertising credits. The gang has been spotted before using malware to steal Facebook-related information and hijack associated business accounts to run their own ads that are paid for by the victim.
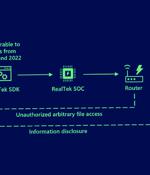
Microsoft said its own investigation into the attack activity uncovered Boa as a common link, assessing that the intrusions were directed against exposed IoT devices running the web server. "Despite being discontinued in 2005, the Boa web server continues to be implemented by different vendors across a variety of IoT devices and popular software development kits," the company said.

A nascent and legitimate penetration testing framework known as Nighthawk is likely to gain threat actors' attention for its Cobalt Strike-like capabilities. There are no indications that a leaked or cracked version of Nighthawk is being weaponized by threat actors in the wild, Proofpoint researcher Alexander Rausch said in a write-up.

The best line of defense against holiday hacking schemes is a comprehensive incident response strategy that focuses on end-user vulnerabilities. The heightened number of cybersecurity threats around the holidays underscore just how important it is to have a comprehensive incident response strategy in place, protecting both your employees and your company's digital infrastructure.

Microsoft said today that security vulnerabilities found to impact a web server discontinued since 2005 have been used to target and compromise organizations in the energy sector. The attackers gained access to the internal networks of the hacked entities via Internet-exposed cameras on their networks as command-and-control servers.

The best line of defense against holiday hacking schemes is a comprehensive incident response strategy that focuses on end-user vulnerabilities. The heightened number of cybersecurity threats around the holidays underscore just how important it is to have a comprehensive incident response strategy in place, protecting both your employees and your company's digital infrastructure.

Sports betting company DraftKings said today that it would make whole customers affected by a credential stuffing attack that led to losses of up to $300,000. The statement follows an early Monday morning tweet saying that DraftKings was investigating reports [1, 2, 3, 4] of customers experiencing issues with their accounts.

A developing threat activity cluster has been found using Google Ads in one of its campaigns to distribute various post-compromise payloads, including the recently discovered Royal ransomware. "Observed DEV-0569 attacks show a pattern of continuous innovation, with regular incorporation of new discovery techniques, defense evasion, and various post-compromise payloads, alongside increasing ransomware facilitation," the Microsoft Security Threat Intelligence team said in an analysis.
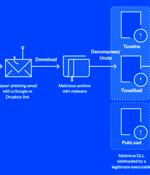
A notorious advanced persistent threat actor known as Mustang Panda has been linked to a spate of spear-phishing attacks targeting government, education, and research sectors across the world. Mustang Panda, also called Bronze President, Earth Preta, HoneyMyte, and Red Lich, is a China-based espionage actor believed to be active since at least July 2018.