Security News

A threat actor claims to be selling public and private data of 400 million Twitter users scraped in 2021 using a now-fixed API vulnerability. The alleged data dump is being sold by a threat actor named 'Ryushi' on the Breached hacking forum, a site commonly used to sell user data stolen in data breaches.

Hackers are actively targeting a critical flaw in YITH WooCommerce Gift Cards Premium, a WordPress plugin used on over 50,000 websites. YITH WooCommerce Gift Cards Premium is a plugin that website operators to sell gift cards in their online stores.

LastPass revealed today that attackers stole customer vault data after breaching its cloud storage earlier this year using information stolen during an August 2022 incident. Toubba added in a new update to the original statement that Lastpass' cloud storage was accessed using "Cloud storage access key and dual storage container decryption keys" stolen from its developer environment.

According to NCC Group's Global Threat Intelligence team, November saw a 41% increase in ransomware attacks from 188 incidents to 265. In its most recent Monthly Threat Pulse, the group reported that the month was the most active for ransomware attacks since April this year.

The notorious FIN7 hacking group uses an automated attack system that exploits Microsoft Exchange and SQL injection vulnerabilities to breach corporate networks, steal data, and select targets for ransomware attacks based on financial size. Next, FIN7's internal 'marketing' team scrutinizes new entries and adds comments on the Checkmarks platform to list victims' current revenue, number of employees, domain, headquarters details, and other information that helps pentesters determine if the firm is worth the time and effort of a ransomware attack.

Okta, a company that provides identity and access management services, disclosed on Wednesday that some of its source code repositories were accessed in an unauthorized manner earlier this month. The security event, which was first reported by Bleeping Computer, involved unidentified threat actors gaining access to the Okta Workforce Identity Cloud code repositories hosted on GitHub.

More zero knowledge attacks, more leaked credentials, more Gen-Z cyber crimes - 2022 trends and 2023 predictions. As the internet of things continues to develop, cybercriminals will have access to a greater number of vulnerable devices, allowing them to carry out more sophisticated attacks.
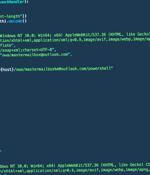
Threat actors affiliated with a ransomware strain known as Play are leveraging a never-before-seen exploit chain that bypasses blocking rules for ProxyNotShell flaws in Microsoft Exchange Server to achieve remote code execution through Outlook Web Access. "The new exploit method bypasses URL rewrite mitigations for the Autodiscover endpoint," CrowdStrike researchers Brian Pitchford, Erik Iker, and Nicolas Zilio said in a technical write-up published Tuesday.

As VP of Research at Pentera, Alex Spivakovsky leads a team of former pen-testers, red-teamers, and incident response experts whose job is to bypass existing security controls. In this Help Net Security video, Spivakovsky discusses the misconception that hackers are waiting by their computers, monitoring the latest CVE announcements, and constructing plans to breach a company by exploiting the CVE. It's a backward way of thinking about the hacking process because, to a hacker, a CVE is a tool, not a strategy.

The PyPi python package repository is being bombarded by a wave of information-stealing malware hiding inside malicious packages uploaded to the platform to steal software developers' data. The malware dropped in this campaign is a clone of the open-source W4SP Stealer, responsible for a previous widespread malware infection on PyPI in November 2022.