Security News

Google on Thursday shipped emergency patches to address two security issues in its Chrome web browser, one of which it says is being actively exploited in the wild.Clément Lecigne of Google's Threat Analysis Group has been credited with reporting the flaw on April 13, 2022.

Google is issuing fixes for two vulnerabilities in its Chrome web browser, including one flaw that is already being exploited in the wild. The emergency updates the company issued this week impact the almost 3 billion users of its Chrome browser as well as those using other Chromium-based browsers, such as Microsoft Edge, Brave and Vivaldi.

Google has released Chrome 100.0.4896.127 for Windows, Mac, and Linux, to fix a high-severity zero-day vulnerability actively used by threat actors in attacks. "Google is aware that an exploit for CVE-2022-1364 exists in the wild," Google said in a security advisory released today.

A popular Windows 11 ToolBox script used to add the Google Play Store to the Android Subsystem has secretly infected users with malicious scripts, Chrome extensions, and potentially other malware. While there were ways to use ADB to sideload Android apps, users began looking for methods that let them add the Google Play Store to Windows 11.

Google on Monday disclosed that it's taking legal action against a nefarious actor who has been spotted operating fraudulent websites to defraud unsuspecting people into buying non-existent puppies. "The actor used a network of fraudulent websites that claimed to sell basset hound puppies - with alluring photos and fake customer testimonials - in order to take advantage of people during the pandemic," Google's CyberCrime Investigation Group manager Albert Shin and senior counsel Mike Trinh said.

Google pulled a slew of Android apps with more than 46 million downloads from its Google Play Store after security researchers notified the cloud giant that the code contained some sneaky data-harvesting code. Google removed the apps as of March 25, but said they could be re-listed if they removed the dodgy code to comply with Google Play Store's rules for collecting users' data.

Researchers have found the info-stealing Android malware Sharkbot lurking unsuspected in the depths of the Google Play store under the cover of anti-virus solutions. While analyzing suspicious applications on the store, the Check Point Research team found what purported to be genuine AV solutions downloading and installing the malware, which steals credentials and banking info from Android devices but also has a range of other unique features.
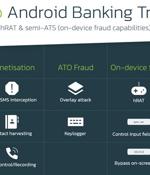
A number of rogue Android apps that have been cumulatively installed from the official Google Play Store more than 50,000 times are being used to target banks and other financial entities. Like other Android banking trojans, the rogue apps are nothing more than droppers, whose primary function is to deploy the malicious payload embedded within them.

Google has announced several key policy changes for Android application developers that will increase the security of users, Google Play, and the apps offered by the service. These new developer requirements will take effect between May 11th through November 1st, 2022, giving developers enough time to adjust to the new changes.
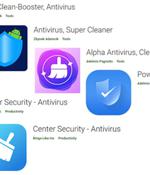
As many as seven malicious Android apps discovered on the Google Play Store masqueraded as antivirus solutions to deploy a banking trojan called SharkBot. "SharkBot steals credentials and banking information," Check Point researchers Alex Shamshur and Raman Ladutska said in a report shared with The Hacker News.